Adaptive Visibility – Breadth and Depth in Simulated Ransomware Attacks by MITRE ATT&CK R4
By Carlos Diaz, Leandro Costantino · April 04, 2022
In our last blog defensive capabilities we outlined how an “alert driven solution is not enough to support the mission of a SOC (Security Operations Center)”, and why a SOC needs high quality visibility surrounding the context of a triggered alert to expedite the outcomes of investigations/hunting workflows. This blog will focus on our adaptive purpose-built visibility and how the Trellix portfolio evolved since the last round, from our foundations of essential visibility to have established a 98% visibility in 2022 MITRE Engenuity ATT&CK® Evaluation (Round4).
Evaluation Overview
The 2022 MITRE Engenuity ATT&CK® Evaluation (Round4) focused on the adversary emulation of Wizard Spider + Sandworm Team known for targeting global organizations and resulting in high value loss from ransom extortions. The focus for this round was to demonstrate the abuse of “Data Encrypted for Impact (T1486)” by those threat actors.
The testing scope lasted 4 days. The first 3 days were focused on detection efficacy with our products set to monitor and report only, while the last day focused entirely on protection – our products set to blocking mode.
NOTE: The goal of these evaluations by MITRE Engenuity is not to rank or score products
Our analysis of the evaluation results found that our blue team was able to use the Trellix portfolio, to obtain significant visibility, achieving:
| Scenario | Evaluation Scope | Visibility Outcome |
| Wizard Spider | Across 10 attack Phases comprised of 52 sub-steps | 98% 51 of 52 sub-steps |
| Sandworm Team | Across 9 attack Phases comprised of 57 sub-steps | 100% 57 of 57 sub-steps |
Defensible Components, the foundation of our visibility.
We introduced Defensible Components in the Round 3 Visibility Blog as the foundation to obtain the required capabilities of an outcomes-driven detection program.
This year, specific sensors were added across the Trellix product lines to augment the defensible components based on the adversary’s behaviors and breach patterns used in ransomware campaigns.
One example was how “Scripting” and “Layer 7 http(s)” telemetry is essential to track the intentions of an attacker thereby enabling the defender to adapt to the intensity of the attack, and correlate various actionable contexts which expedite automated responses as we have covered in our approach with Human Machine Teaming.
The table below represents Trellix Defensible Components and visibility acquired during this evaluation.
| MITRE EVALUATION DATASOURCES IN SCOPE | ENDPOINT (ENS/EDR) | SIEM | MWG | SANDBOX (ATD) | TRELLIX DEFENSIBLE COMPONENT |
|---|---|---|---|---|---|
| PROCESS MONITORING | ✔ | ✔ | ✔ | Process | |
| DLL MONITORING | ✔ | ✔ | ✔ | DLL | |
| FILE MONITORING | ✔ | ✔ | ✔ | File | |
| NETWORK TRAFFIC/MONITORING | ✔ | ✔ | ✔ | ✔ | Network (*)TLS INSPECTION |
| SANDBOX, SYSTEM CALLS/API MONITORING | ✔ | ✔ | API (**)COM INSPECTION (**)WINHTTP/WININET |
||
| AMSI/SCRIPT LOGS | ✔ | ✔ | ✔ | Script (VBS/JS/PowerShell) |
|
| WINDOWS REGISTRY | ✔ | ✔ | ✔ | Windows Registry | |
| WINDOWS EVENT LOGS | ✔ | ✔ | ✔ | Windows Events Log (Driver Load/App Logs/ Firewall / Firmware) |
|
| NAMED PIPES | ✔ | ✔ | Named Pipe | ||
| WMI OBJECTS | ✔ | ✔ | WMI | ||
| AUTHENTICATION LOGS | ✔ | ✔ | ✔ | ✔ | Authentication/Authorization |
| ETW/WINDOWS EVENT LOGS | ✔ | ✔ | Services/ Scheduled Task | ||
| DOMAIN NAME | ✔ | DNS Queries | |||
| LOGON SESSION | ✔ | ✔ | Authentication/Authorization |
(**) New in EDR 4.0
(*) Web Gateway and Web SaaS Service
NOTE: If a product is configured differently, you can obtain information from each Defensible Component, but this represents telemetry acquired based on the configuration used in the evaluation.
Scenario 1 – Wizard Spider
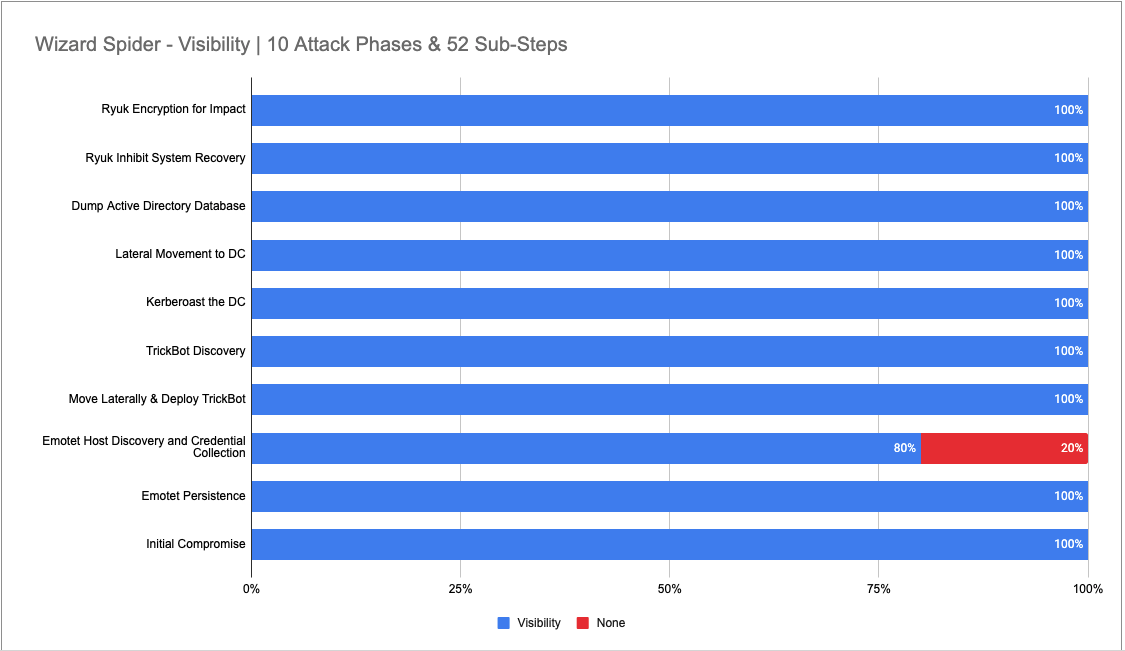
The Wizard Spider emulation consisted of an attack with 10 Major Steps (Kill Chain Phases) on day one, and our portfolio provided visibility across every phase – our minimum visibility was 80% in Step 3 – Emotet Host Discovery. In these 10 phases, MITRE conducted 52 sub-steps to emulate the behaviors aligned to the known TTPs attributed to the Wizard Spider adversary.
Our visibility design resulted in 98% or 51 of 52 sub-steps.
Scenario 2 – Sandworm Team
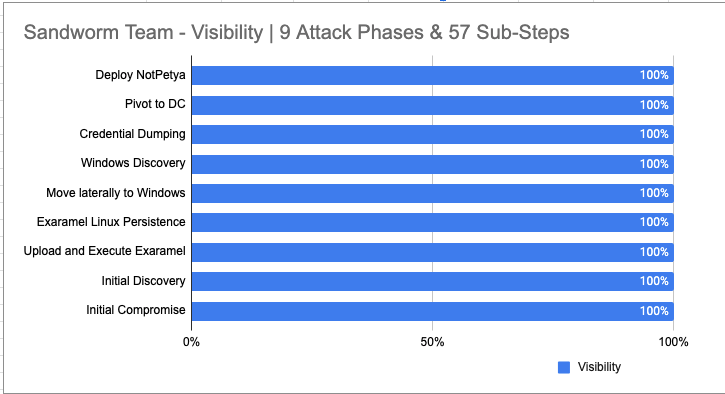
The Sandworm Team emulation consisted of an attack with 9 Major Steps (Kill Chain Phases) on day two, and our portfolio provided visibility across every phase. In these 9 phases, MITRE conducted 57 sub-steps to emulate the behaviors aligned to the known TTPs attributed to the SANDWORM TEAM adversary.
Our visibility design resulted in 100% or 57 of 57 sub-steps.
Visibility By Data Sources / Defensible Components
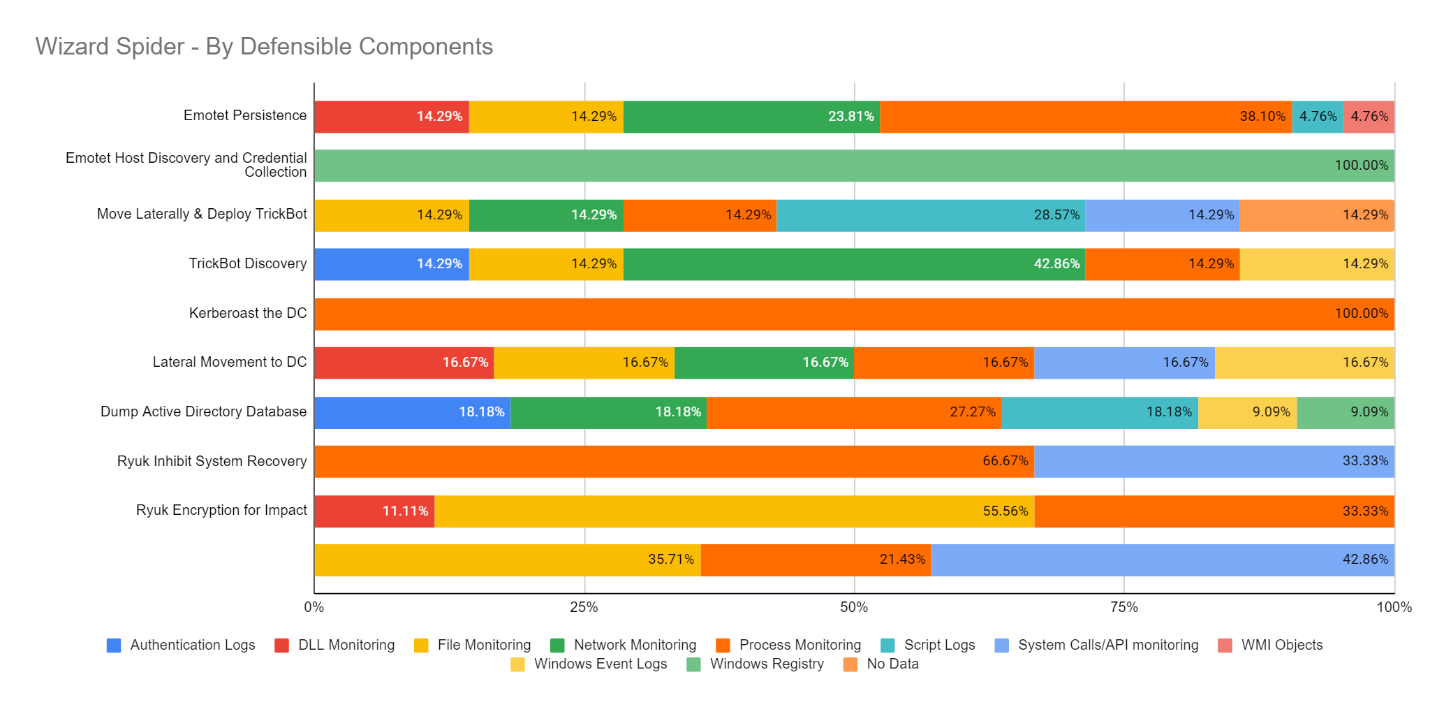
Scenario 1 – Wizard Spider
Of the 52 Sub-Steps emulating Wizard Spider, our visibility coverage extends from more than 22 unique data sources including ATD sandbox integration, capable of intercepting script source code without human intervention thanks to the DXL integration.
NOTE: Defensible components presented here are based on what MITRE focused on, it does not represent the entirety/availability of the Trellix portfolio
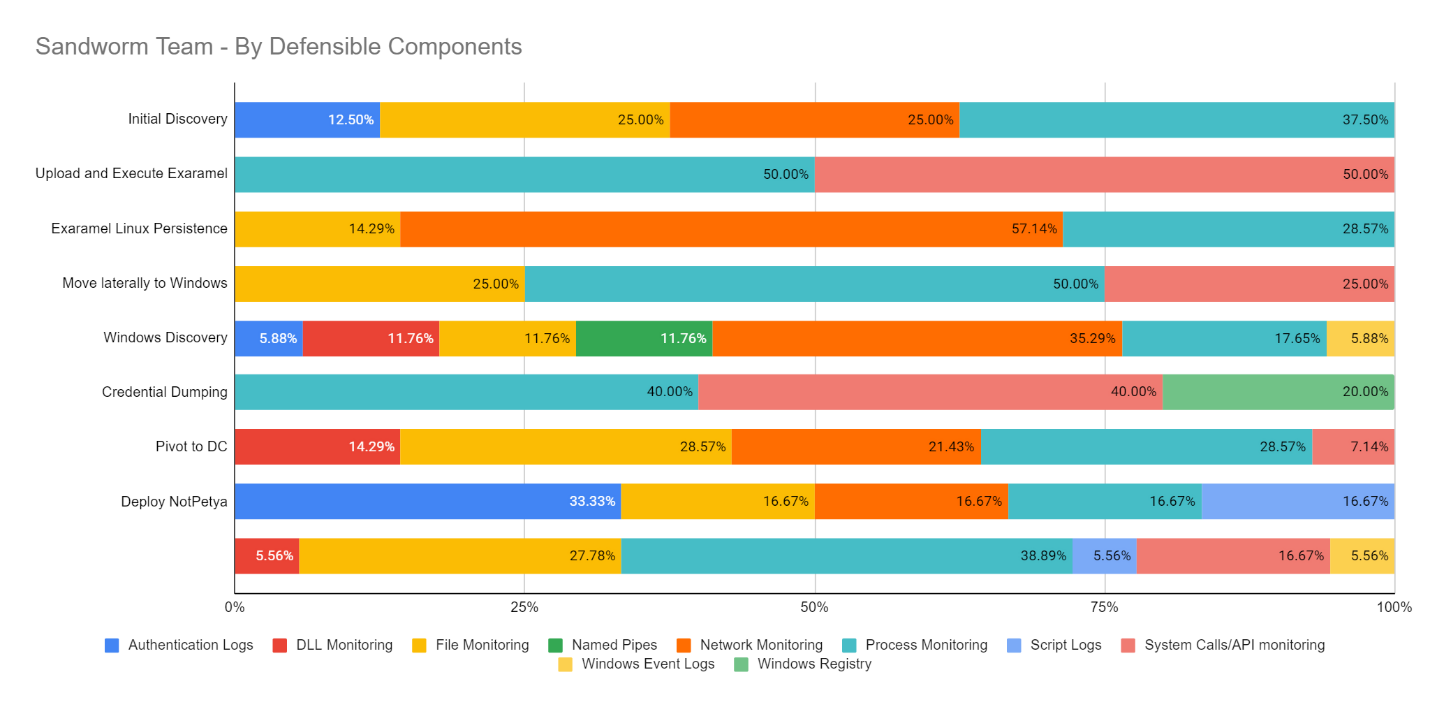
Scenario 2 – Sandworm Team
Of the 59 Sub-Steps emulating the SANDWORM TEAM, our visibility coverage extends from more than 20 unique data sources providing higher context in critical phases with Network and API Calls Monitoring providing awareness of the adversary behaviors in most important stages of the attack.
Visibility on Prevalent Techniques
Scenario 1 – Wizard Spider
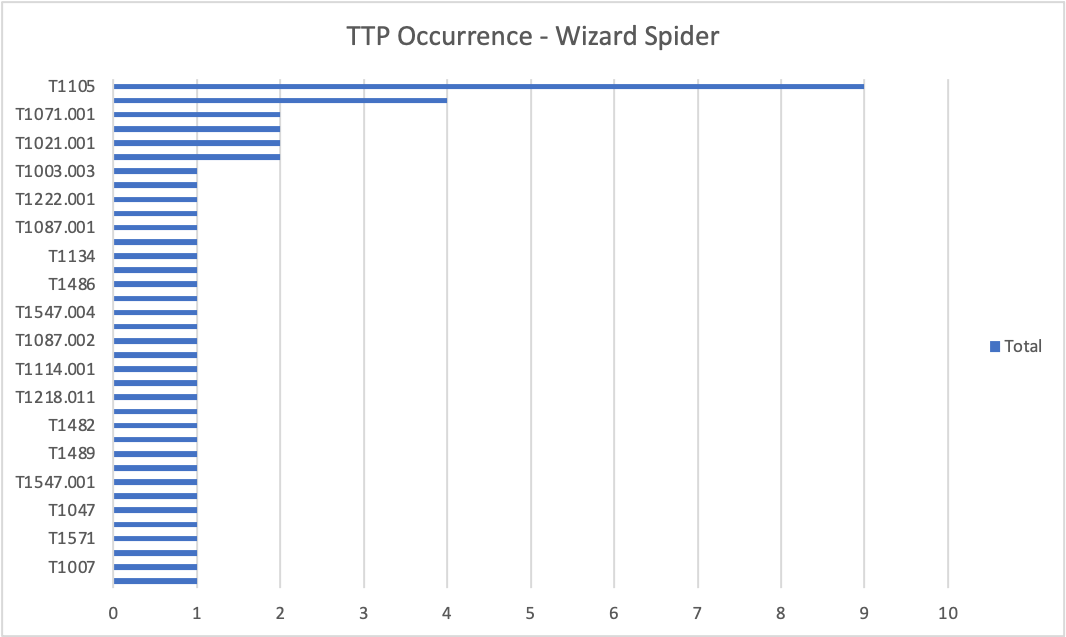
The most prevalent techniques are Ingress Tool Transfer followed by Application Layer Protocol (Web Protocols). Our ATD Sandbox, EDR+EPP and Gateway worked flawlessly intercepting different vectors for the same technique in most cases. Lastly, it’s worth to mention that ENS (EPP) provided insightful information about Data Encrypted for Impact (T1486) when rundll32 encrypted various files using AES.
The rich visibility acquired from these different sensors and products were key to effectively detect this technique when executed in both server and workstation devices – e.g., Api Sensors, Memory Sections, Filesystem Actions.
Additionally, these diverse telemetry sources result in behavioral activity (events) which when correlated allows us our customers to see the full picture with greater detail. Consequently, seeing the full picture empowers blue-teamers to have contextual-awareness of the situation so they can take purposeful actions during the attack – i.e., hunting, containing, mitigating, and eradicating nefarious behaviors.
Scenario 2 – Sandworm Team
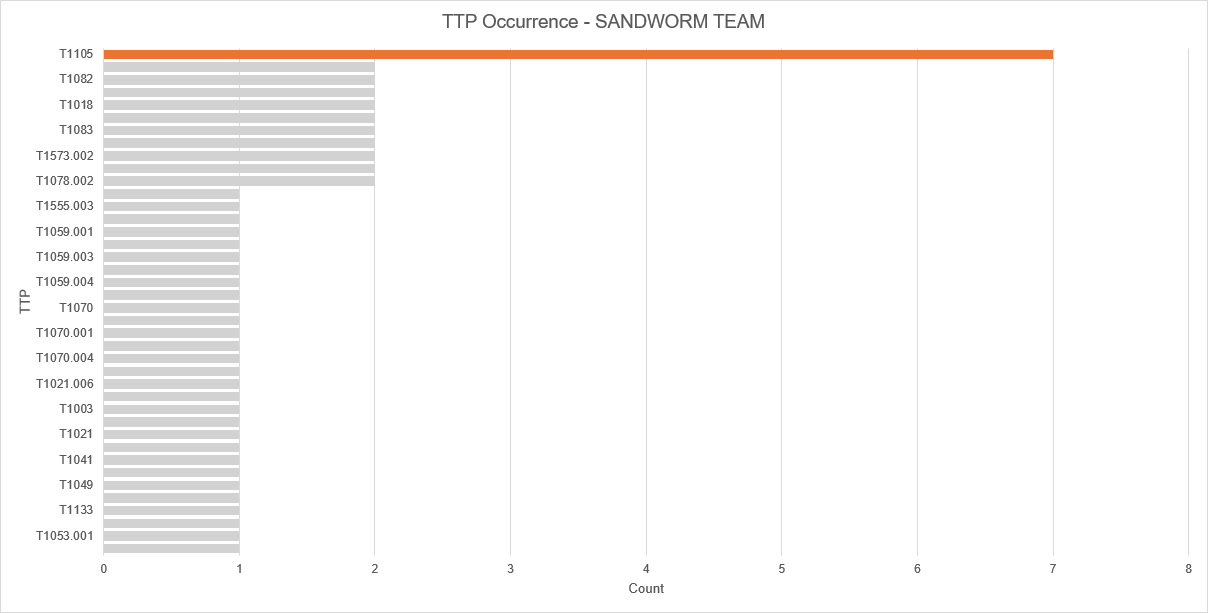
In the SANDWORM TEAM scenario things were consistent with the WIZARD-SPIDER scenario, however, we recognize how the T1105 Ingress Tool Transfer technique and other network-oriented techniques were exercised many times, therefore proving our anticipations for Layer 7 network visibility being critical. Our customers can count on our diverse coverage but in-depth provision of this critical network visibility.
Final Thoughts
We understand visibility is paramount for our customers, below is a graph that explains how our detection strategy was supported to reduce alert fatigue, and the details from our detection team can be referenced here.
The following 113 detections were produced by telemetry from multiples data sources.
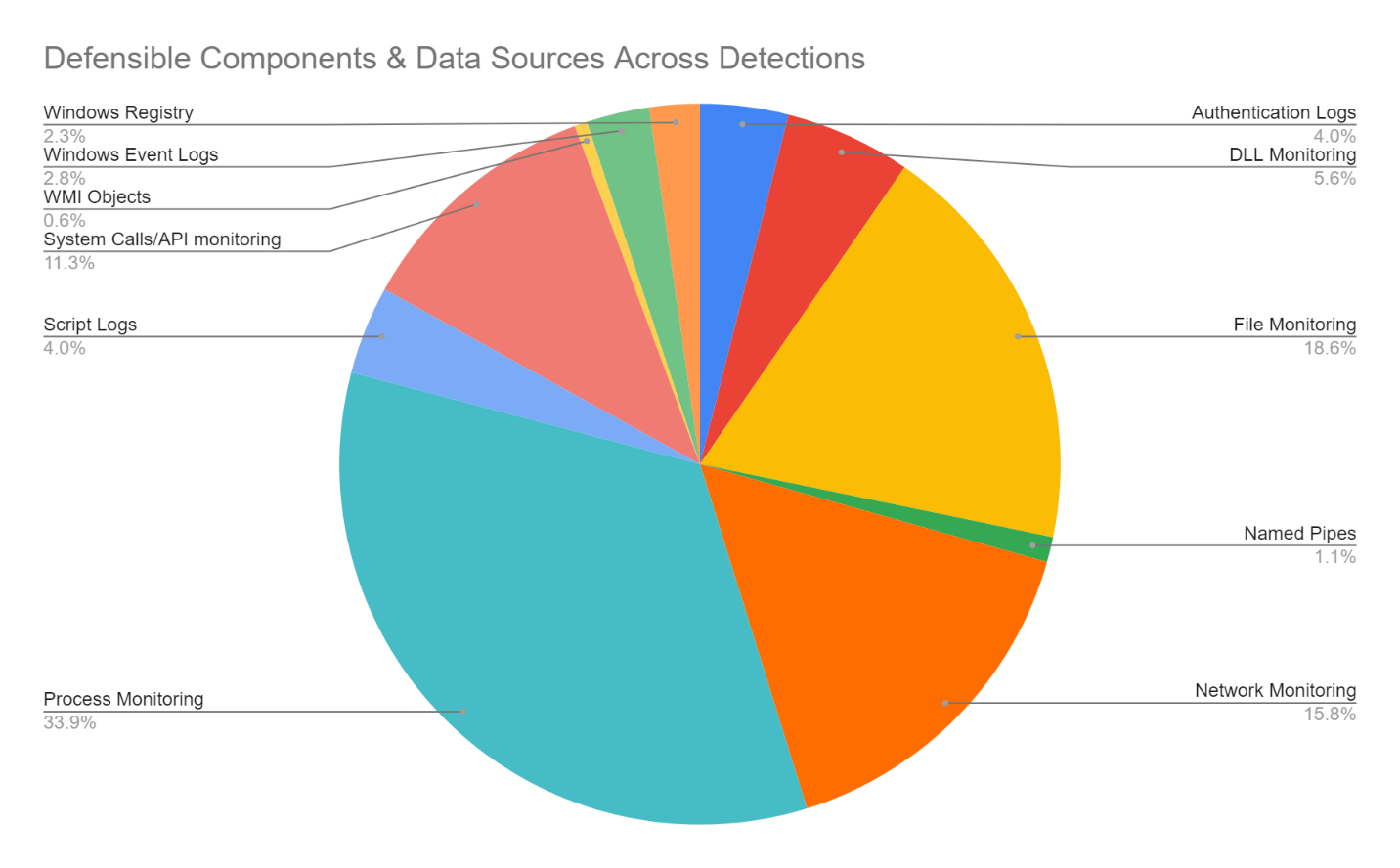
Afterall, to analyze and contextualize data, you MUST have excellent telemetry foundations to acquire useful and valuable information from impacted systems. It’s not just a matter of creating sensors and providing raw data. A strong design requires that this information be correlated across Defensible Components.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.