Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Bug Report – January 2023 Edition
By Trellix · February 1, 2023
This story was also written by Jesse Chick.

Why am I here?
Welcome to the Bug Report, Space-Hash™ Edition! (Think about it. We'll wait.) For many of us, January began with a headache on a Sunday morning and, if you happen to be on the receiving end of this month's remote code excitement, it may have ended with one, too. So, whether you've been with us from the beginning or are hopping on the bandwagon now, please remember to hydrate, and enjoy these tasty morsels from our "in the wild" menu.
- CVE-2022-47966: ManageEngine OnPremise
- CVE-2022-44877: Control Web Panel
- CVE-2023-21674: Windows ALPC
And if you find yourself still hungry for more, be sure to check out Trellix HAX 2023, the latest iteration of our annual CTF competition, slated to launch on February 25th. While it's still a few weeks out, you can join the Discord server today to get updates and chat with the organizers (us) directly. If you need further convincing, the top 5 teams can get their grubby paws on the gorgeous challenge coin linked above.
Enough self-promotion - back to the bugs!
CVE-2022-47966: A very APT new year to you!
What is it?
A supply chain vulnerability in the login mechanism for a dizzying array of ManageEngine products, which can lead (and has led) to remote code execution. The affected products, broadly geared toward infrastructure management and security, leveraged an ancient version (1.4.1) of Apache Santuario for SAML enforcement during authentication. This version contains an issue tracked since 2008 where clients can inject malicious XML and execute code via the Java Runtime Environment before Santuario has verified the integrity of the payload. (For the curious among you, a complete root cause analysis with pretty pictures is available courtesy of the good folks at Horizon3.ai.) To make matters worse and headaches achier, exploitation requires no authentication whatsoever, as the vulnerability exists in the means of authentication itself.
Who cares?
According to enlyft, ManageEngine products are used by nearly 10,000 companies worldwide across all sectors, including several which deal with highly sensitive information such as healthcare, financial services, and government. If that's you, your care factor had better be quite high. GreyNoise detected numerous exploitation attempts involving CVE-2022-47966 starting on January 19th, so, in the worst case, threat actors may have already made a nest for themselves in server racks across the globe.
It may take the edge off slightly to point out that this vulnerability is contingent. The vendor claims that "ManageEngine On-Demand/cloud products are not affected by this vulnerability," only the OnPremise product suite. Among those products, CVE-2022-47966 applies only to hosts for which single sign-on is configured. For some of the products, SSO must be enabled for it to be vulnerable; for others, it need only have been enabled at some point in the past. ManageEngine's security advisory notes which conditions apply to each product.
What can I do?
Don't dwell on the irony of a vendor who issues software updates not bothering to update themselves in over a decade, much less in a timely manner; doing so will not bring any joy, only despair. Instead, carefully review the security advisory addressing CVE-2022-47966 and cross-reference the list of vulnerable products and version numbers with those used by your organization. Are any of those products present in your infrastructure? Then update all ManageEngine software immediately. No? Still update all ManageEngine software. If you conclude that any machine was vulnerable prior to taking these measures, we advise scouring the logs for indicators of compromise.
CVE-2022-44877: Don't quote me on this...
What is it?
The tabloids might introduce CVE-2022-44877 as "Handsome Turkish researcher finds gaping hole in popular web hosting tool." We, being the serious and sober-minded security professionals that we are, will introduce CVE-2022-44877 as "an unauthenticated remote code execution vulnerability in Control Web Panel (CWP), a free GUI for managing Linux systems." At least the folks at ManageEngine aren't alone in the doghouse, right?
This time, the vulnerability takes the form of a Linux command injection in – you guessed it – the login page of CWP. The vulnerability itself is quite easy to understand given the requisite Bash scripting knowledge (and is therefore even more galling). Each time an incorrect login attempt is received by CWP, certain information parsed from the request, including the unsanitized (!) and client-controlled (!!!) value of the "login" URL parameter, is appended to a local file as a means of record-keeping. In all versions of CWP prior to 0.9.8.1147, this was done using the beloved echo command followed by a double-quoted string containing whatever the client included in the URL after "login=". The use of double quotes means that any valid Linux command enclosed in $(...), such as a command to download and run malware, will be executed before the echo process exits. Oops...
Who cares?
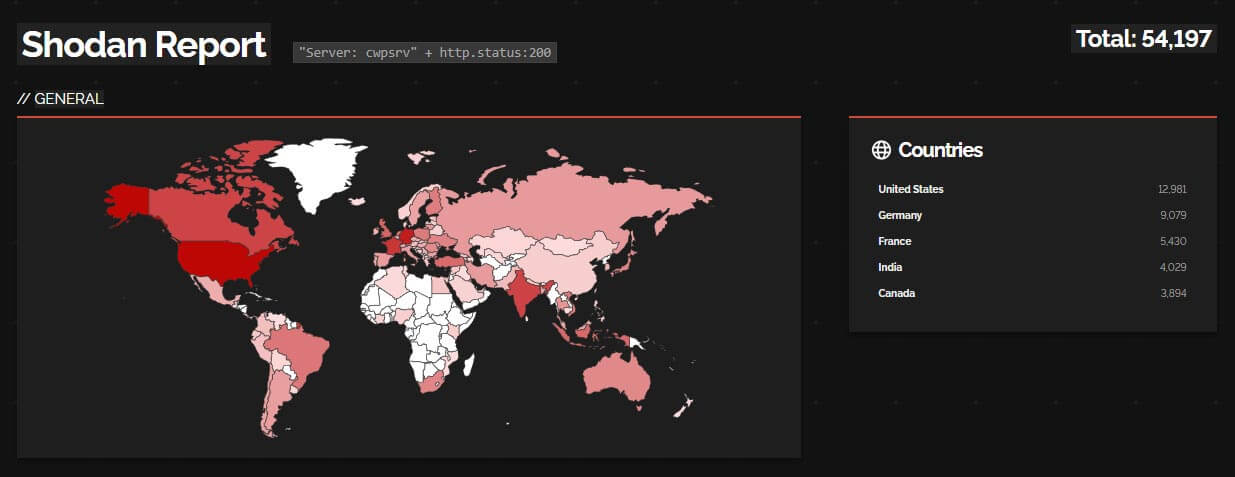
If your organization uses a version of CWP prior to 0.9.8.1147, this is a certified two-handed head-clutcher. The CWP homepage claims there are 35,000 servers running CWP and Shodan suggests this number could be understated solely among hosts reachable from the broader internet. A great rule of thumb in cases like this is to care more than threat actors do, and threat actors care a lot.

Following the release of proof-of-concept code on the discovering researcher's GitHub on January 6th, the floodgates opened to exploitation attempts. On the 17th, CISA dutifully added Control Web Panel to its must-patch list.
What can I do?
If you chose to indulge in the convenience of exposing your CWP instance to the internet during the pandemic (or did so for any other reason), then your first mitigating step should be to take it offline. It’s hard for someone to break into your house if they can’t darken your doorstep.
Next, check for indicators of compromise. According to GreyNoise, there are several hosts worldwide which have attempted to exploit CVE-2022-44877. If any of these IPs appear in your logs, you can be confident that your system was at least targeted. Pretty sure “all publicity is good publicity” doesn’t apply here.
Finally, be sure to update to the latest version of Control Web Panel. As of this writing, that would be version 0.9.8.1149. If you are diligent in checking for and acting on new releases for your infrastructure, you may already be in the clear: this vulnerability was addressed by version 0.9.8.1147, released on October 25th of 2022.
And, at risk of fostering complacency among the sysadmins of the world, we are happy to report that Trellix IPS customers are covered via the signature ‘HTTP: Control Web Panel Login Command Injection Vulnerability (CVE-2022-44877),’ having signature ID 0x452c0800. Customers should make sure to get the latest signature set updates to receive protections for this and a litany of other vulns that didn’t make our January Wall of Infamy.
CVE-2023-21674: Uh… what are you doing on my corporate machine?
What is it?
Our last item on the docket is a cute little elevation of privilege affecting the latest versions of Windows – in both its server and desktop incarnations. The flaw itself exists in the Advanced Local Procedure Call (ALPC) implementation, a local analog to RPC which is used internally by the Windows OS for interprocess communication. Were we to base conclusions merely on the names and CVSS vectors accompanying the roster of Microsoft vulnerabilities addressed on last month's Patch Tuesday, this one probably would not drop any jaws. However, size is not as important as how you use it, and, according to CISA, threat actors are definitely using it. Given that local access is required to exploit CVE-2023-21674, this vulnerability is likely to be used in concert with others as part of an attack chain. That is not to diminish its significance at all; the difference between operating within a restrictive group policy and having carte blanche to install malware and open backdoors on a captured host represents a decisive difference for APTs, particularly since CVE-2023-21674 can be used to achieve browser sandbox escape.
Who cares?
Surprise, surprise: almost everyone. Like it or not, Windows in the workplace is still the modern orthodoxy, and Windows server holds a hefty chunk of the market share as well. If your org is an exception to this, we hereby salute your rebel spirit, and you need not bother yourself with the Windows attack surface.

What can I do?
Microsoft released a patch for CVE-2023-21674 on Patch Tuesday, so if your Windows infrastructure is configured for automatic updates, then you're probably in the clear already. This is probably a good practice in general, for both Windows servers and desktops, to eliminate the element of human attention span from your internal update cycle. If TikTok is any indication, this is a resource in short supply. If updating is not possible, for whatever reason, Trellix Network Security provides detection for CVE-2023-21674 via rule ‘Exploit.CVE-2023-21674.’ Those using our IPS product are similarly covered via the signature ‘HTTP: Microsoft Windows ALPC Elevation of Privilege Vulnerability (CVE-2023-21674),’ having signature ID 0x452bdf00.
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
