Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
LockBit3.0: A Threat that Persists
By Trellix · November 17, 2022
This blog was written by Alexandre Mundo
LockBit is a very well-known family of ransomware that has created havoc worldwide over the last few years. In March 2022, a new variant of the ransomware was discovered. The LockBit3.0 variant presented with a mix of previous code from the LockBit family and code from the now defunct nefarious Black Matter ransomware.
This updated version is built to spread chaos and encrypt all files in the infected system, just as previous versions of LockBit, but now has new layers of protection and tricks to make analysis and detection more difficult.
In this blog, we will provide technical analysis into a sample with the hash ed555f0162ea6ec5b8b8bada743cfc628d376274
Technical details
This sample is a Win32 application that can run in older operating systems as well. It has a first layer of protection that may look like a new technique, but is actually an old trick used in other types of malware.
All malware is encrypted with an unknown packer/layer that requires a special key and argument to decrypt the real malware and execute it.
In this case, the malware is executed following the “-pass” argument and later the key to decrypt it.
This type of protection is enough to avoid researchers without the key analyzing the sample. Nevertheless, if a protected system has any type of logging mechanism that can capture the command line of the application, this special key can be captured in the log.
After this layer of protection, the malware has strong obfuscation using tricks borrowed from Black Matter.
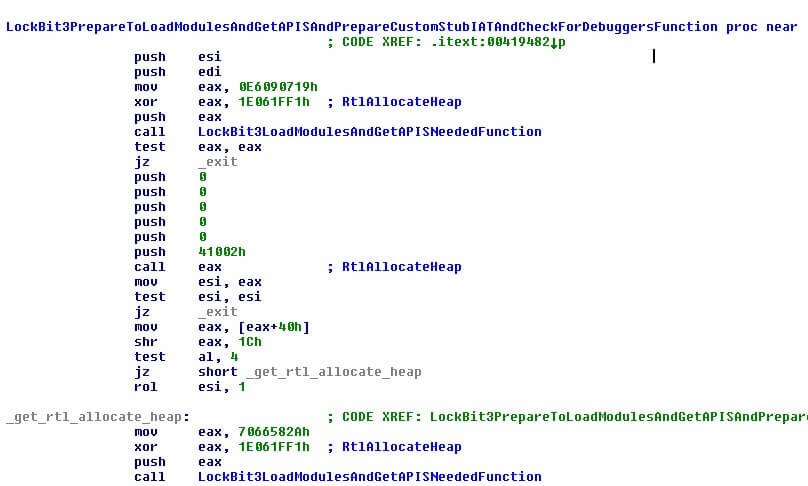
After the first layer, the malware begins loading the modules needed and the APIs required.
Like Black Matter, the LockBit3.0 code uses a technique to try obfuscating the APIs using a Stack Obfuscation running 32 bit values as hashes.
With this technique, it is impossible to know which APIs and modules are used, but they can be determined with a debugger or using tools like Hash DB.
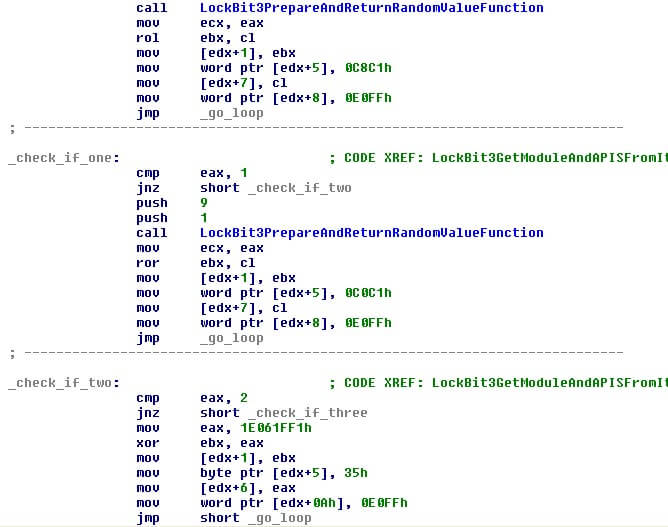
Black Matter ransomware typically obfuscates APIs using a special stub that is made in runtime. This is done through the following process:
- Reserve memory
- The malware will choose a random number and based in the result will prepare a special code that will try to obfuscate the calls to the APIs. LockBit3.0 has five types of code it can make. This is done to make detection more difficult.
- The malware will acquire the API memory address and obfuscate the address that the stub will decrypt and jump later. The malware will obfuscate the final entry point to the API that will later call in this new code to make harder the analysis.
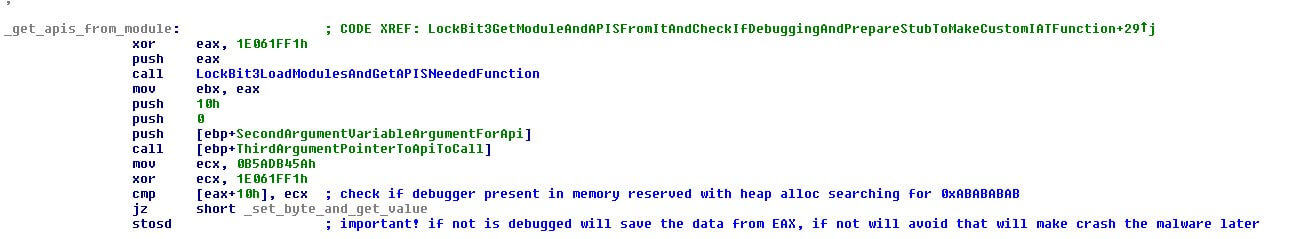
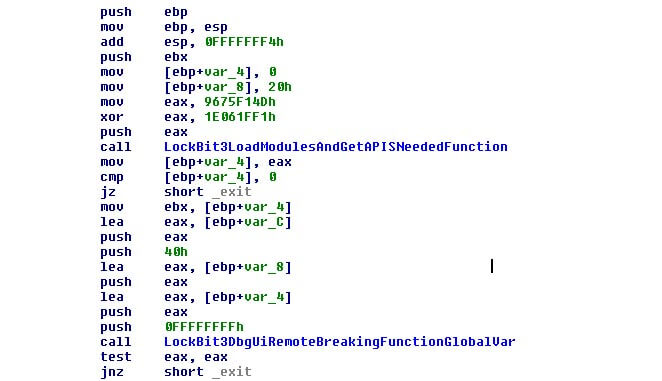
Just as with Black Matter, prior to making the stub, it will check to see if a debugger is attached and if so, the stub will stop functioning. In this case, the malware will crash in the moment it calls any API.
The debugger check is done with a trick to check if the memory has the values 0xABABABAB.
LockBit3.0 has another protection mechanism built in and uses the API “SetThreadInformation” to see if the thread escapes from the debugger. If found, the malware will run but any debugger will be stopped from debugging it.
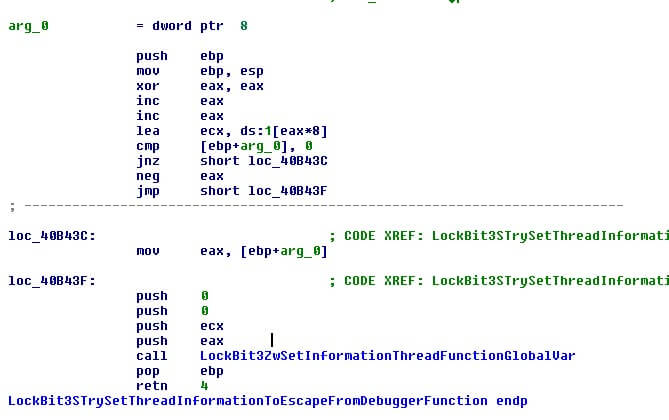
Following these steps the malware will use the API “DbgUiRemoteBreaking” to ensure a debugger stops working. This closely aligns with the work of Black Matter malware developers to make their samples hard to analyze.
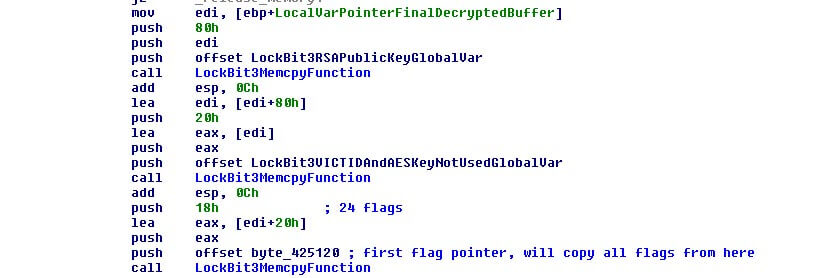
LockBit3.0 has an internal configuration that is encrypted and compressed with different blocks that can be encrypted too and encoded in base64. We see this in Black Matter as well, except while Black Matter will have 10 flags, LockBit3.0 has 24 to expand the options available to malware operators.
By focusing on the flags and other important parts in the configuration, we have this structure:
PUBLIC_KEY [0x80]
RSA Public Key used in the malware
VICT_ID [0x10]
ID to track the victim. Legacy from Black Matter, don´t use in LockBit v3
AES_KEY [0x10]
AES KEY used in Black Matter, kept in the malware as legacy. Don´t use it.
FLAGS [0x18]
Manage the behavior of the malware, 24 in LockBit v3 instead 10 as in Black Matter.
POINTER_STRUCT_TO_DATA
A struct that keep the size in byte for each config struct with strings encoded in base64 as in Black Matter.
DATA_ENCODED_IN_BASE64
A struct of different blocks that keep each one different data in encoded strings (and crypted) as (but not limited only to):
- Services to stop and kill
- Process to terminate
- Ransom note template
- Files, folders, and extensions to avoid in the crypto process.
Similar to Black Matter, LockBit3.0 requires a lot of work to extract and prepare the configuration fields:
It’s interesting to note that the malware decrypts in memory along with the ransom note template, creation of the victim ID and writing of the ransom note, before encrypting again in memory for later use.
By encrypting the ransom note in memory, the user can avoid detection by security products that can detect this pattern.
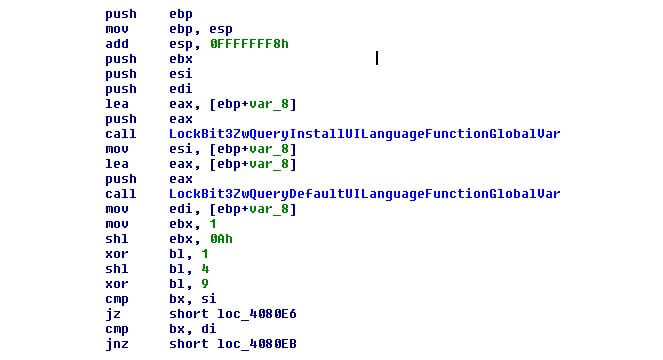
Like other ransomware, LockBit3.0 will check the flag to compare the language of the victim machine with a hardcoded list of blacklisted languages. If this flag is enabled, it will check the language using two APIS “ZwQueryInstallUILanguage” and “ZwQueryDefaultUILanguage”.
With these two functions, it checks the normal use language and the install language of the Windows system. The checks are done against a list of hardcoded values in code but obfuscated to try avoiding detection in disk and make analysis that much more difficult.
Some of the languages that are voided with LockBit3.0 are:
- Russian from Russia
- Ukrainian from Ukraine
- Romanian from Moldova
- Belarusian
- Tatar
- Georgian from Georgia
If the malware detects one of these languages, it will stop the execution and refrain from hurting the system in any way.
Like we see with Black Matter, LockBit3.0 will also try different tricks to elevate privileges and escalate:
- Duplicate token from SVCHOST.EXE and other processes as EXPLORER.EXE
- Using PEB, it will launch different shellcodes if the operating system is 32 or 64 bits. In the case of 32 bits it’ll be used only once, but in the case of 64 bits, it will be used twice which causes an argument the second one
Later, the malware will make the new extension for the encrypted files, the icon of the encrypted files and the ransom note.
Unlike Black Matter, which reads the “MachineGUID” from the registry, this new version of LockBit uses the RSA Public Key block and calculate a MD5 hash from it.
This change is done for two reasons:
- First, to avoid Anti-Virus protections that check to see if “MachineGUID” is manipulated to avoid that the malware executing. If this happens with Black Matter, the malware stops without any real damage in the victim machine.
- Second, to make it easier to track the extension files to one malware operator and victims.
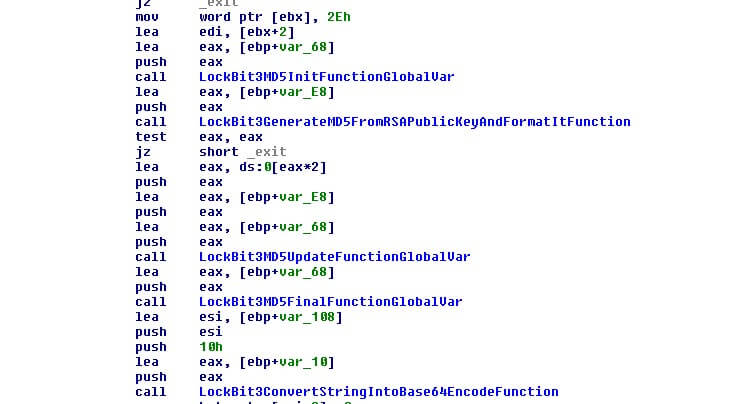
This string makes the ransom note name file and calculates a hash to check the integrity of the file name later.
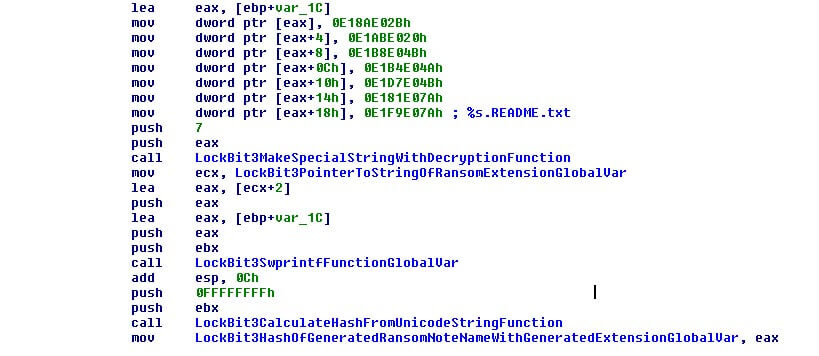
The malware then creates a special icon file that is hardcoded in the binary in the %appdata% folder in the victim system with the same name as the ransom note but with the extension “.ico”.
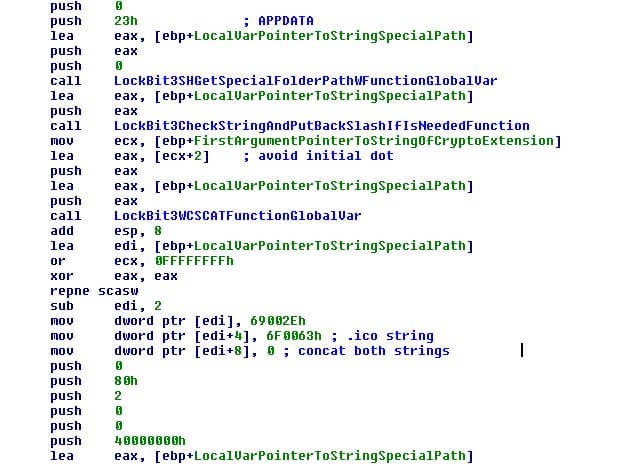
Later in the registry, the LockBit3.0 writes file associated with the encrypted files and the new extension so the user will only have encrypted files shown with this new icon to warn the user.
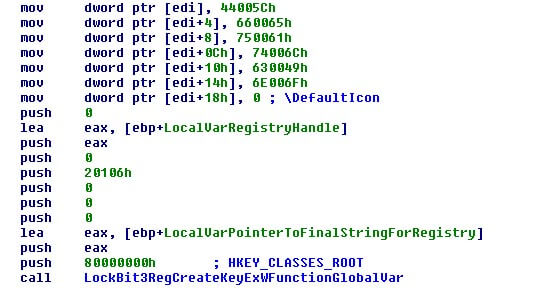
These changes are applied in the system using the API “SHChangeNotify” which forces the system to update all changes the moment it is called.
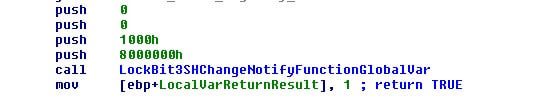
LockBit3.0 has 24 flags that can change its behavior. Some of these flags are:
CRYPT_WITH_RANDOM_NAMES
If enabled, the malware will encrypt the files and will rename it with a random name but with the extension already prepared.
ENCRYPT_BIG_FILES
If enabled, big files will be encrypted, in other case they would be avoided to more quickly damage the system. A operator want crypt files very quickly, avoiding big files is a way to sure that a big damage can be done very quickly.
AVOID_HIDDEN_FILES
If enabled, the malware will avoid the files that have this flag in the file's properties.
MAKE_LOGON
If enabled, the malware will try to make a login attempt with the credentials that are stored in the configuration. In the case that is not enabled, or the credentials block is empty will avoid it.
CHECK_LANGUAGE
If set, the malware will check the language of the victim machine as is explained in this report.
ENCRYPT_SHARED_FOLDERS
If set, the malware will try encrypting shared folders, other cases will be avoided.
ENCRYPT_SERVER
If set, the malware will try encrypting all volumes that can be mounted and all exchange servers that can found, other cases will be avoided.
CREATE_MUTEX
If set, the malware will try make a mutex to avoid multiple executions in the victim machine, as can be used to make anti-virus this flag usually can be set to disabled.
DELETE_SERVICE
If set, the malware will try to find, stop and delete services in a services block in the configuration. This behavior is for security to avoid be detected and to avoid stopping encryption process but is a noisy behavior.
KILL_PROCESSES
If set, the malware will try, as with services, to find and terminate processes in the configuration block. This is to avoid be detected and protect the encryption process but is a noisy behavior.
CHANGE_WALLPAPER
If set, the malware will change the desktop´s wallpaper in the victim machine to alert the users about the attack in the machine.
CHANGE_ICON
If set, the malware will try drop the special hardcoded icon file as is explained in this report and set this icon as default icon for the encrypted files extension. In some samples this flag won’t be checked, making the set of the icon always.
PRINT_RANSOM_NOTE
If set, the malware will try print the ransom note in all available printers that can found to alert the users about the attack in the machine. This behavior can be very noisy and stop other activities of the companies.
DELETE_MALWARE
If is set will try delete itself when your attack finish to try don´t left any trace in disk about the malware file.
DELETE_AV_SERVICES
If set, the malware will try stop and delete an AV services stored in one block in the configuration.
CONNECT_TO_C2
If set, the malware will try connecting and send information, as Black Matter does, about the victim, machine, and files encrypted.
The encryption process is remarkably like Black Matter.
Conclusion
LockBit3.0 is a new variant of the LockBit family that adds code from Black Matter to increase protections against detection and slow its analysis. By increasing the number of flags to have more behaviors, malware operators have more flexibility to leverage the malware in different scenarios. Notably, the malware has been used in attacks, like the attack to “Entrust” on June 18, 2022.
This malware is serious threat that should be watched and controlled through patching systems against vulnerabilities, closing RDP connections that are not needed, phishing education to employees, and taking measures to protect servers and critical stations.
IOC
ED555F0162EA6EC5B8B8BADA743CFC628D376274
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
