Triton Malware Spearheads Latest Attacks on Industrial Systems | McAfee Blogs
Thomas Roccia · NOV 08, 2018
Malware that attacks industrial control systems (ICS), such as the Stuxnet campaign in 2010, is a serious threat. This class of cyber sabotage can spy on, disrupt, or destroy systems that manage large-scale industrial processes. An essential danger in this threat is that it moves from mere digital damage to risking human lives. In this post we will review the history of ICS malware, briefly examine how one ICS framework operates, and offer our advice on how to fight such threats.
ICS malware is usually sophisticated, requiring time to research its targets and sufficient resources. Attackers can be motivated by financial gain, hacktivism, or espionage, as well as for political ends, as we saw with Stuxnet. Since Stuxnet, researchers have discovered several industrial attacks; each year we seem to read about a worse threat than before.
In August 2017, a sophisticated malware targeted petrochemical facilities in the Middle East. The malware—dubbed Triton, Trisis, or HatMan—attacked safety instrumented systems (SIS), a critical component that has been designed to protect human life. The system targeted in that case was the Schneider Triconex SIS. The initial vector of infection is still unknown, but it was likely a phishing attack.
After gaining remote access, the Triton attackers moved to disrupt, take down, or destroy the industrial process. The goal of the attackers is still unclear because the attack was discovered after an accidental shutdown of the plant led to further investigation. Investigations conducted by several security companies have revealed a complex malware framework embedding PowerPC shellcode (the Triconex architecture) and an implementation of the proprietary communication protocol TriStation. The malware allowed the attackers to easily communicate with safety controllers and remotely manipulate system memory to inject shellcodes; they completely controlled the target. However, because the attack did not succeed it is possible that a payload, the final stage of the attack, was missing. All investigations pointed in this direction. If the final payload had been delivered, the consequences could have been disastrous.
CVE-2022-22620: Apple finally gave something away for free!
History of ICS malwareIn 2010, Stuxnet was one of the most sophisticated ICS threats discovered. This cyber weapon was created to target Iranian centrifuges. It was able to reprogram a particular programmable logic controller to change the speed of centrifuge rotations. The goal of Stuxnet was not to destroy but to take the control of the industrial process.
In 2013, the malware Havex targeted energy grids, electricity firms, and many others. The attackers collected a large amount of data and remotely monitored industrial systems. Havex was created for espionage and sabotage.
BlackEnergy was discovered in 2015. It targeted critical infrastructure and destroyed files stored on workstations and servers. In Ukraine, 230,000 people were left in the dark for six hours after hackers compromised several power distribution centers.
In 2015, IronGate was discovered on public sources. It targeted Siemens control systems and had functionalities similar to Stuxnet’s. It is unclear if this was a proof of concept or a simple penetration-testing tool.
Industroyer hit Ukraine again in 2016. The malware embedded a data wiper component as well as a distributed denial of services module. It was crafted for destruction. The attack caused a second shutdown of Ukraine’s power grid.
In 2017, Triton was discovered. The attack did not succeed; the consequences could have been disastrous.

ICS malware are critical because they infect industrial devices and automation. However, regular malware can also impact industrial process. Last year WannaCry forced several companies, from medical to automobile industries, to stop production. Some months later NotPetya hit nuclear power plants, power grids, and health care systems. In 2018, a cryptocurrency miner struck a water utility in Europe.
Facing widespread risks, critical infrastructures need a specific approach to stay safe.
ICS malware are critical because they infect industrial devices and automation. However, regular malware can also impact industrial process. Last year WannaCry forced several companies, from medical to automobile industries, to stop production. Some months later NotPetya hit nuclear power plants, power grids, and health care systems. In 2018, a cryptocurrency miner struck a water utility in Europe.
Triton framework
Triton targeted the Triconex safety controller, distributed by Schneider Electric. Triconex safety controllers are used in 18,000 plants (nuclear, oil and gas refineries, chemical plants, etc.), according to the company. Attacks on SIS require a high level of process comprehension (by analyzing acquired documents, diagrams, device configurations, and network traffic). SIS are the last protection against a physical incident.
The attackers gained access to the network probably via spear phishing, according to an investigation. After the initial infection, the attackers moved onto the main network to reach the ICS network and target SIS controllers.
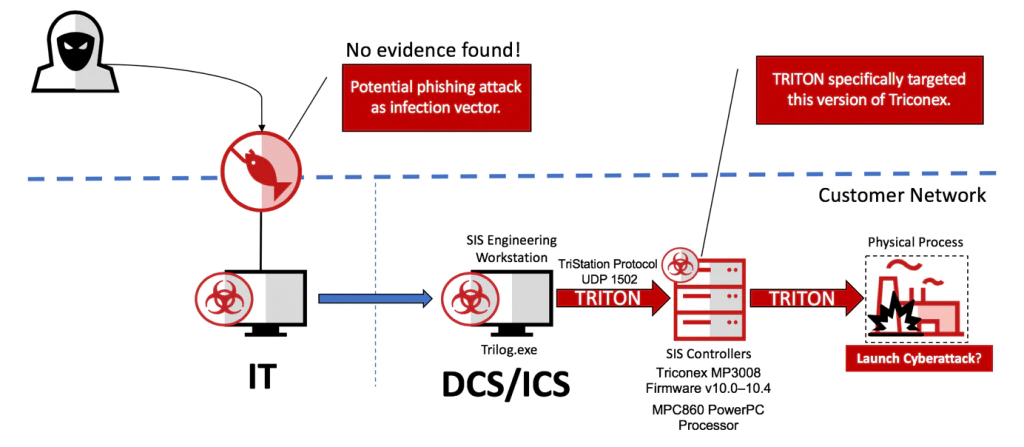
To communicate with SIS controllers, attackers recoded the proprietary TriStation communication protocol on port UDP/1502. This step suggests they invested the time to reverse engineer the Triconex product.
Nozomi Networks has created a Wireshark dissector that is very handy for analyzing the TriStation protocol and detecting a Triton attack. The following screenshot shows an example of the information returned by the Triconex SIS. Triton requires the “running state” of the controller to perform the next stages of the attack.
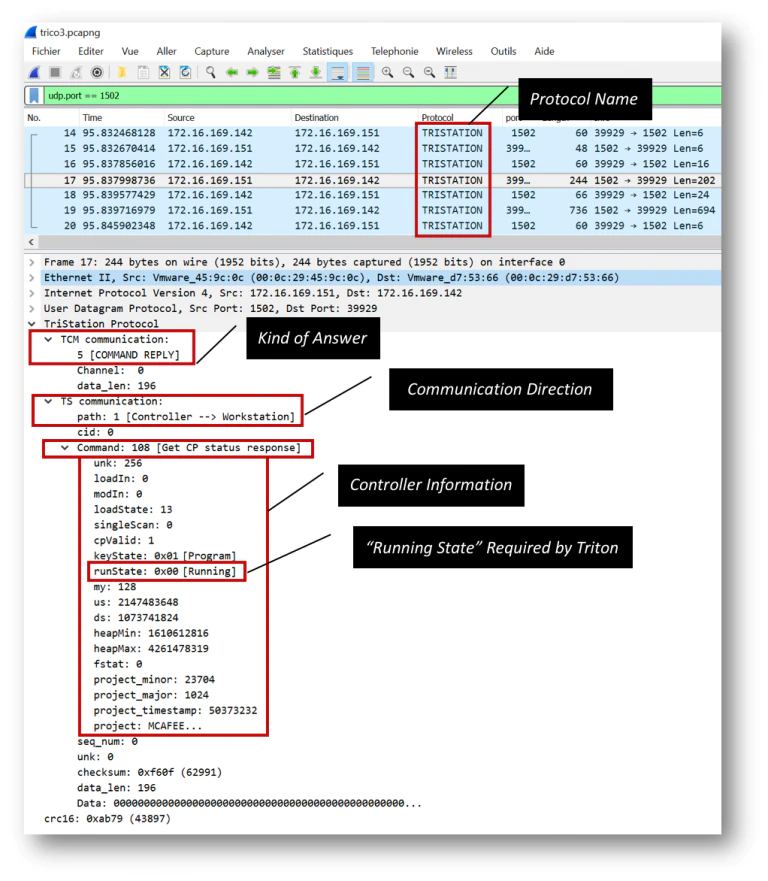
In the preceding screen Triconex replies to the request “Get Control Program Status,” which is sent by Triton.
The Triton framework (dc81f383624955e0c0441734f9f1dabfe03f373c) posed as the legitimate executable trilog.exe, which collects logs. The executable is a python script compiled in an exe. The framework also contains library.zip (1dd89871c4f8eca7a42642bf4c5ec2aa7688fd5c), which contains all the python scripts required by Triton. Finally, two PowerPC shellcodes (the target architecture) are used to compromise the controllers. The first PowerPC shellcode is an injector (inject.bin, f403292f6cb315c84f84f6c51490e2e8cd03c686) used to inject the second stage (imain.bin, b47ad4840089247b058121e95732beb82e6311d0), the backdoor that allows read, write, and execute access on the Triconex product.
The following schema shows the main modules of Triton:
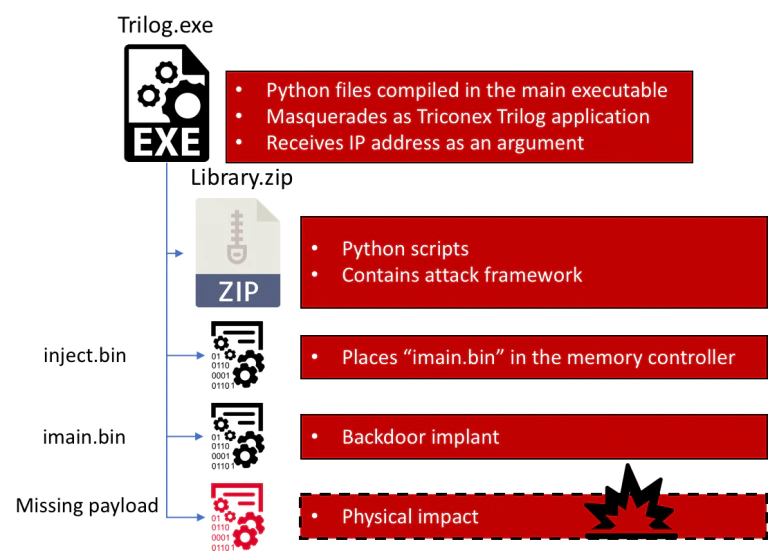
The missing payload has not been recovered during the forensic investigation. Because the attack was discovered early, it is possible that the attackers did not have time to launch the final stage.
How to detect an unusual network connection
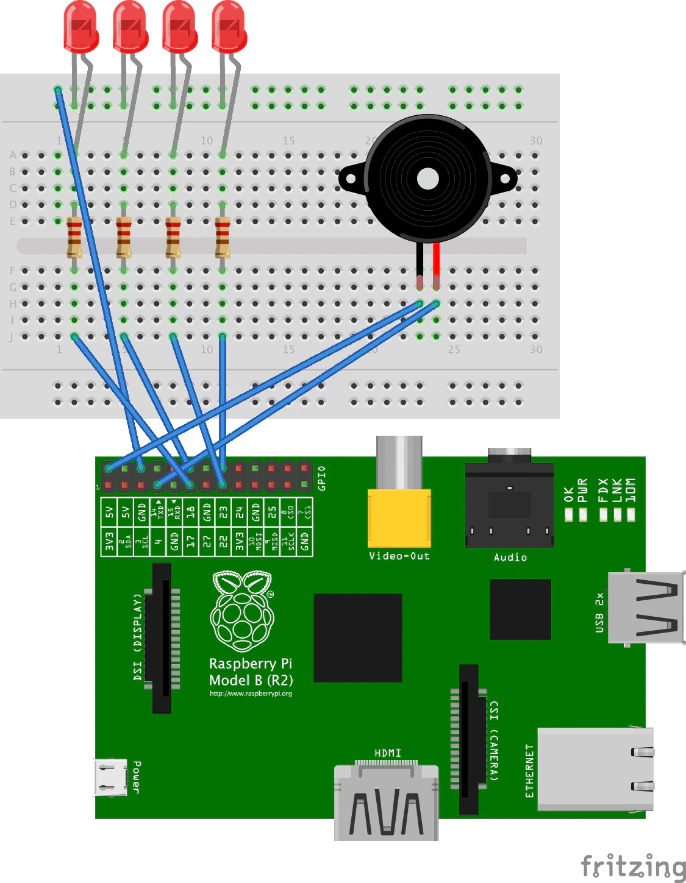
Nozomi Networks has created a script that simulates a Triconex safety controller. We modified this script with a Raspberry Pi to create a cheap detector tool.
This inexpensive tool can be easily installed on an ICS network. If an illegitimate connection occurs, the device alerts with a blinking LED and siren. It also displays the IP address of the connection for further investigation.
The following picture shows how to connect the LED and buzzer.
Fighting ICS malware
ICS malware has become more aggressive and sophisticated. Many industrial devices were built before anyone imagined cyberattacks such as Triton. ICS’s are now exposed to connected environments they were not designed for.
Standard McAfee security recommendations (vulnerability patching, complex passwords, identification control, security tools, etc.) remain the same as for regular networks, yet industrial systems also require specific procedures due to their importance. Industrial networks must be segregated from general business networks, and every machine connected to the industrial process should be carefully monitored by using strict access control and application whitelisting.
Further security recommendations:
- Segregate physical and logical access to ICS networks with strong authentication, including strong passwords and double factor, card readers, surveillance cameras, etc.
- Use DMZ and firewall to prevent network traffic from passing between the corporate and the ICS network
- Deploy strong security measures on the ICS network perimeter, including patch management, disabling unused ports, and restricting ICS user privileges
- Log and monitor every action on the ICS network to quickly identify a point of failure
- When possible implement redundancy on critical devices to avoid major issues
- Develop strong security policies and an incident response plan to restore systems during an incident
- Train people with simulated incident responses and security awareness
Attackers learn what works from past attacks and from each other. Rapid developments in ICS threats make it crucial to stay protected. Manufacturers, plant operators, governments, and the cybersecurity industry must work together to avoid critical cyberattacks.
Indicators of compromise
- dc81f383624955e0c0441734f9f1dabfe03f373c: trilog.exe
- b47ad4840089247b058121e95732beb82e6311d0: imain.bin
- f403292f6cb315c84f84f6c51490e2e8cd03c686: inject.bin
- 91bad86388c68f34d9a2db644f7a1e6ffd58a449: script_test.py
- 1dd89871c4f8eca7a42642bf4c5ec2aa7688fd5c: library.zip
- 97e785e92b416638c3a584ffbfce9f8f0434a5fd: TS_cnames.pyc
- d6e997a4b6a54d1aeedb646731f3b0893aee4b82: TsBase.pyc
- 66d39af5d61507cf7ea29e4b213f8d7dc9598bed: TsHi.pyc
- a6357a8792e68b05690a9736bc3051cba4b43227: TsLow.pyc
- 2262362200aa28b0eead1348cb6fda3b6c83ae01: crc.pyc
- 9059bba0d640e7eeeb34099711ff960e8fbae655: repr.pyc
- 6c09fec42e77054ee558ec352a7cd7bd5c5ba1b0: select.pyc
- 25dd6785b941ffe6085dd5b4dbded37e1077e222: sh.pyc
References
- https://blog.schneider-electric.com/cyber-security/2018/08/07/one-year-after-triton-building-ongoing-industry-wide-cyber-resilience/
- https://www.youtube.com/watch?v=f09E75bWvkk
- https://ics-cert.us-cert.gov/sites/default/files/ICSJWG-Archive/QNL_DEC_17/Waterfall_top-20-attacks-article-d2%20-%20Article_S508NC.pdf
- https://www.fireeye.com/blog/threat-research/2017/12/attackers-deploy-new-ics-attack-framework-triton.html
- https://www.midnightbluelabs.com/blog/2018/1/16/analyzing-the-triton-industrial-malware
- https://www.nozominetworks.com/2018/07/18/blog/new-triton-analysis-tool-wireshark-dissector-for-tristation-protocol/
- https://github.com/NozomiNetworks/tricotools
- https://cyberx-labs.com/en/blog/triton-post-mortem-analysis-latest-ot-attack-framework/
- https://vimeo.com/275906105
- https://vimeo.com/248057640
- https://blog.talosintelligence.com/2017/07/template-injection.html
- https://github.com/MDudek-ICS/TRISIS-TRITON-HATMAN
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Featured Content
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.