What Is a Security Operations Center (SOC)?
Reviewed by Grant McDonald · December 18, 2025
The security operation center (SOC) is a 24/7 centralized function within an organization employing people, processes, and technology to continuously monitor and improve an organization's security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents.
Webinar
Meet Trellix Hyperautomation—a true no-code tool for automated security workflows
Put orchestration and automation directly in the hands of your SOC team.
A SOC acts like the hub or central command post, taking in telemetry from across an organization's IT infrastructure. This includes its networks, devices, appliances, and information stores, wherever those assets reside. The proliferation of advanced threats places a premium on collecting context from diverse sources.
Essentially, the SOC is the correlation point for every event logged within the organization that is being monitored. For each of these events, the SOC must decide how to manage and act upon them.
Security operations center roles and responsibilities
The function of a security operations team is to monitor, detect, investigate, and respond to cyber threats around the clock. Security operations teams are charged with monitoring and protecting many assets. These include intellectual property, personnel data, business systems, and brand integrity.
Security operations teams serve as the implementation component of an organization's overall cybersecurity framework. They act as the central point of collaboration in coordinated efforts to monitor, assess, and defend against cyberattacks.
SOCs typically feature a hub-and-spoke architecture. Spokes of this model can incorporate a variety of systems, such as:
- Vulnerability assessment solutions
- Governance, risk and compliance (GRC) systems
- Application and database scanners
- Intrusion prevention systems (IPS)
- User and entity behavior analytics (UEBA)
- Endpoint detection and remediation (EDR)
- Threat intelligence platforms (TIP)
The SOC is usually led by a SOC manager. Other staff may include incident responders, threat hunters, incident response managers, and SOC analysts. Level 1 analysts are on the reactive front line, triaging alerts. Level 2 analysts correlate events, escalate real incidents, and hand off to Level 3 analysts, who lead complex investigations, incident response, and threat research. The SOC reports to the CISO, who in turn reports to either the CIO or directly to the CEO.
Here are 10 key responsibilities of the SOC:
- Take Stock of Available Resources
The SOC manages two types of assets. First are the various devices, processes and applications they’re charged with safeguarding. Second are the defensive tools at their disposal to help ensure this protection.
- What the SOC Protects
The SOC can’t safeguard devices and data they can’t see.. A lack of visibility and control from device to cloud creates blind spots in the network security posture, which malicious actors can find and exploit.
To counter such gaps, the SOC strives to gain a complete view of the organization’s threat landscape. This includes not only the various types of on-premises endpoints, servers, and software, but also third-party services and traffic flowing between these assets.
- How the SOC Protects
The SOC should also have a complete understanding of all cybersecurity tools on hand and all workflows in use within the SOC. This increases agility and allows the SOC to run at peak efficiency levels.
In addition, the SOC maintains security awareness for an organization, performing mock phishing exercises and sharing information about attempted attacks.
- Preparation and Preventative Maintenance
Even the most well-equipped and agile response processes are no match for preventing problems from occurring in the first place. To help keep attackers at bay, the SOC implements preventative measures, which can be divided into two main categories.
- Preparation
Team members should stay informed on the newest security innovations, the latest trends in cybercrime, and the development of new threats on the horizon.
This research can help inform the creation of a security roadmap that will provide direction for the company’s cybersecurity efforts going forward. It can also help shape a disaster recovery plan that will serve as ready guidance in a worst-case scenario.
- Preventative Maintenance
This step includes all actions taken to make successful attacks more difficult. It includes regularly maintaining and updating existing systems; updating firewall policies; patching vulnerabilities; and allowlisting, denylisting, and securing applications.
- Continuous Proactive Monitoring
Tools used by the SOC scan the network 24/7 to flag any abnormalities or suspicious activities. Monitoring the network around the clock allows the SOC to be notified immediately of emerging threats, giving them the best chance to prevent or mitigate harm.
Monitoring tools can include a SIEM or an EDR. Even better would be a SOAR or an integrated security platform.
The most advanced platforms use behavioral analysis to “teach” systems the difference between regular day-to-day operations and actual threat behavior. This capability minimizes the amount of triage and analysis that humans must do.
- Alert Ranking and Management
When monitoring tools issue alerts, the SOC must cut through the noise to surface the true signals of an attack. AI-enabled security capabilities such as Trellix Wise enable SOC teams to automatically investigate all of their data, discard any false positives, and determine how aggressive any actual threats are and what they could be targeting. This allows the SOC to triage emerging threats appropriately, handling the most urgent issues first.
- Threat Response
These are the actions most people think of when they think of the SOC. As soon as an incident is confirmed, the SOC acts as first responder.
The SOC team shuts down or isolates endpoints, terminates harmful processes (or prevents them from executing), and deletes files. It also resets passwords, reverses elevated privileges, returns endpoints to their last good state, and more. The goal is to respond to the extent necessary while having as small an impact on business continuity as possible.
- Recovery and Remediation
In the aftermath of an incident, the SOC will work to restore systems and recover any lost or compromised data. This may include wiping and re-imaging endpoints, reconfiguring systems or, in the case of ransomware attacks, deploying viable backups in order to circumvent the ransomware.
When successful, this step will end disruptions to normal business operations.
- Log Management
The SOC is responsible for collecting, maintaining, and regularly reviewing the log of all activity across the entire organization. Typically using a SIEM, the SOC aggregates and correlates the data feeds from networks, applications, firewalls, operating systems, and endpoints, all of which produce their own internal logs.
This data helps define a baseline for “normal” activity, can reveal the existence of threats, and can be used for remediation and forensics in the aftermath of an incident.
- Root Cause Investigation
In the aftermath of an incident, the SOC is responsible for figuring out exactly what happened when, how, and why. During this investigation, the SOC uses log data and other information to trace the problem to its source, which will help them prevent similar problems from occurring in the future.
- Security Refinement and Improvement
Cybercriminals are constantly refining their tools and tactics. In order to stay ahead of them, the SOC needs to implement improvements on a continual basis. This includes hardening endpoint defenses, creating security playbooks, and deploying additional automation and orchestration to surface threats faster and offload routine tasks.
During this step, the plans outlined in the security road map come to life. This refinement can also include hands-on practices such as red-teaming and purple-teaming, in which security cohorts conduct tests to identify vulnerabilities, enhance defenses, and build resilience against real-world threats.
- Compliance Management
Many SOC processes are guided by established best practices, but some are governed by compliance requirements. The SOC is responsible for regularly auditing their systems to ensure compliance with such regulations. These may be issued by their organization, by their industry, or by governing bodies.
Examples of these regulations include GDPR, HIPAA, and PCI DSS. Acting in accordance with these regulations helps safeguard sensitive data entrusted with the company. It can also shield the organization from reputational damage and legal challenges resulting from a breach.
Optimizing a security operations model
Dealing with incidents monopolizes much of the SOC's resources. However, the CISO is also responsible for the larger picture of risk and compliance.
To bridge operational and data silos across these functions, an effective strategy requires an adaptive security architecture that enables organizations to enact optimized security operations.
This approach increases efficiency through integration, automation, and orchestration. It also reduces the amount of labor hours required while improving your information security management posture.
An optimized security operations model requires the adoption of a security framework that makes it easy to integrate security solutions and threat intelligence into day-to-day processes.
SOC tools like centralized and actionable dashboards help integrate threat data into security monitoring dashboards and reports. This keeps operations and management apprised of evolving events and activities.
By linking threat management with other systems for managing risk and compliance, SOC teams can better manage overall risk posture. Such configurations support continuous visibility across systems and domains.
They can also use actionable intelligence to drive better accuracy and consistency into security operations. Centralized functions reduce the burden of manual data sharing, auditing, and reporting throughout.
The CyberThreat Report
Insights gleaned from a global network of
experts, sensors, telemetry, and intelligence
Best practices for security operations center threat management
Best Practice #1: Conduct a Threat Management Assessment
Operationalizing threat management should start with a thoughtful assessment. In addition to defenses, an organization should evaluate processes and policies.
Ask questions such as:
- Where is the organization strong?
- What are the gaps?
- What is the risk posture?
- What data is collected, and how much of that data is used?
- How can we use AI and automation to augment team capabilities and speed response times?
Best Practice #2: Create a Threat Management Response Plan
While every organization is different, certain core capabilities and security operations best practices represent due care today. A reasonable threat management process is based on a plan that includes:
- Discovery, including baseline calculation to promote anomaly detection, normalization, and correlation. This includes proactive threat hunting, which uses automation and user entity and behavior analytics(UEBA) to identify potential risks.
- Triage, based on risk and asset value.
- Analysis, including contextualization.
- Scoping, including iterative investigation.
Threat management processes feed prioritized and characterized cases into incident response programs. A well-defined response plan is absolutely key to containing a threat or minimizing the damage from a data breach. Incident response playbooks can help teams rapidly put that plan into effect.
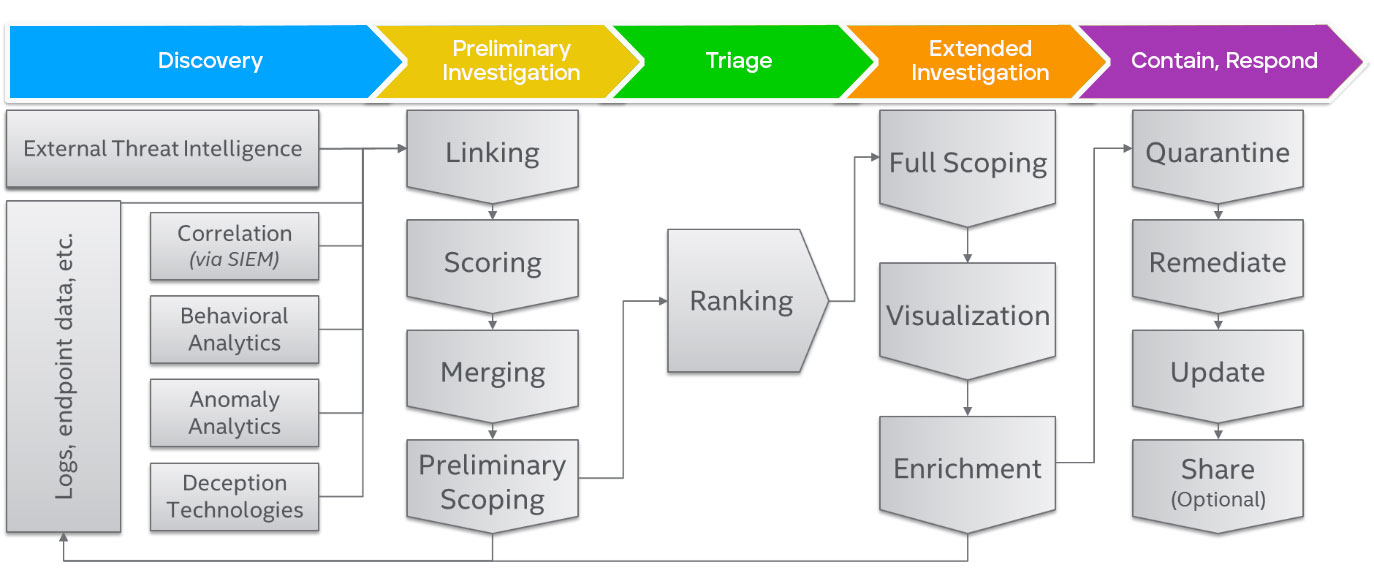
In addition, organizations should focus on training to build skills and uplevel SOC analysts. Increasing collaboration across teams and integrating tools and data provide increased visibility as well.
Best Practice #3: Determine the Right Data to Support Threat Management
Effective visibility and threat management will draw on many data sources, but it can be hard to sort out what is useful and timely information. AI can help by automatically investigating alerts, using the full context of your data to determine when teams need to take action.
The most valuable data has proven to be the following:
- Event data produced by countermeasures and IT assets
- Indicators of compromise (IoCs) produced internally via malware analysis
- IoCs produced externally via threat intelligence feeds
- System data available from sensors such as host, network, database, etc.
Data sources like these are not just an input to threat management. They also add context and make the information valuable and actionable for more precise, accurate, and speedy assessment throughout the iterative and interactive threat management effort.
Access to, and effective use of, the right data to support plans and procedures is a measure of organizational maturity. A "mature" scenario would include a workflow that hands off the right information or permits direct action within operational consoles and across products. This flow integrates IT operations and security teams and tools into incident response when there is a critical event.
Best Practice #4: Review Threat Management Effectiveness
These assessments will help prioritize where an increase in investment or reduction of friction is needed to make threat management implementation match goals. Tracking KPIs such as mean time to detect (MTTD) and mean time to respond (MTTR) provides evidence to support such investments.
Consultants and penetration tests can help benchmark strategy and organizational maturity. They can also health check security responses against attacks to obtain a current measure of an organization’s ability to detect and contain malicious events.
By comparing against peer enterprises, this vetted review can help justify and explain the need to redirect or invest in cybersecurity operations resources.
Security operations center (SOC) FAQ
A SOC typically incorporates a variety of systems, such as
- Vulnerability assessment solutions
- Governance, risk and compliance (GRC) systems
- Application and database scanners
- Intrusion prevention systems (IPS)
- User and entity behavior analytics (UEBA)
- Endpoint detection and remediation (EDR)
- Threat intelligence platforms (TIP)
- Conducting a threat management assessment
- Creating a threat management response plan
- Determining the right data to support threat management
- Reviewing threat management effectiveness
Security operations center (SOC) resources

Learn how Trellix can unite your SOC teams, tools, and processes.

Find out how to achieve extended visibility, multilayered threat detection, and accelerated investigation and response into network traffic.

Discover how to reduce your attack surface, detect stealthy threats, and rapidly remediate threats, as well as how to identify and contain the blast radius.
Grant McDonald, Director, Product Marketing Security Operations, has over 17 years of experience working in Cybersecurity across a range of technologies including Endpoint, Server Security, Cloud and Data Security. At Trellix he is focused on Security Operations and the Trellix Platform. When he isn't writing, speaking or increasing cybersecurity awareness he enjoys restoring old cars, skiing, and watching the latest entertainment from a galaxy far, far away.